RAM-6021 Wired Router
31
Admin Tab
2.3.3.3
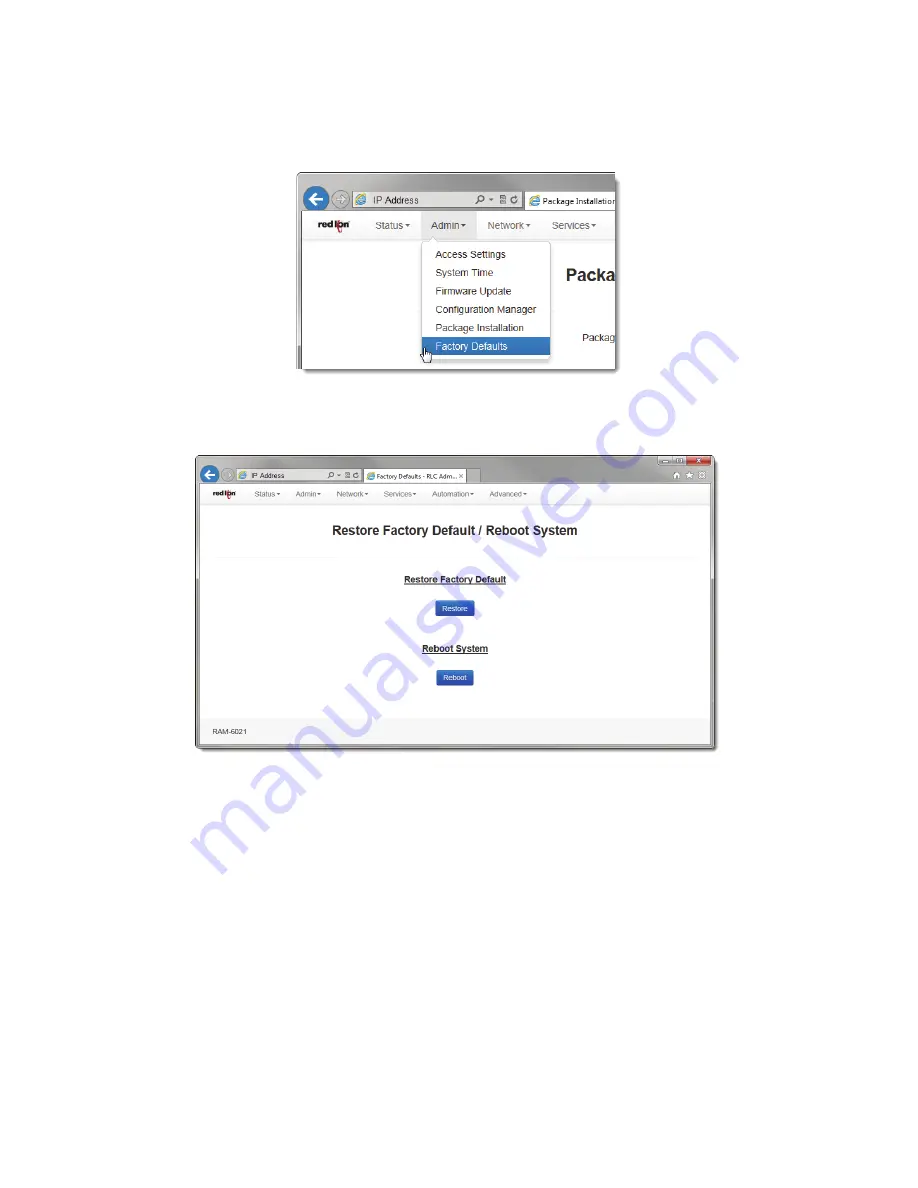
Factory
Defaults
The
Factory
Defaults
menu
item
allows
you
to
restore
the
configuration
back
to
factory
default
settings.
•
Click
on
the
Factory
Defaults
menu
item
and
the
following
window
will
appear:
Restore
Factory
Default:
Click
on
the
Restore
button
to
restore
the
factory
default
settings.
A
warning
will
appear,
read
through
the
information
and
click
OK.
The
restore
may
take
2
‐
5
minutes.
Reboot
System:
Click
on
the
Reboot
button
to
reboot
the
device.
A
warning
will
appear,
read
through
the
information
and
click
OK.
The
reboot
may
take
2
‐
5
minutes.
















































