Configuring Administrator Authentication
Administrator authentication requires the login user name and password for verifying administrators
attempting to specify the machine's settings or access them from a network. When registering an
administrator, you cannot use a login user name already registered in the Address Book. Administrators
are managed differently from the users registered in the Address Book. Windows authentication and
LDAP authentication are not performed for an administrator, so an administrator can log in even if the
server is unreachable due to a network problem. Each administrator is identified by a login user name.
One person can act as more than one type of administrator if multiple administrator privileges are
granted to a single login user name. For instructions on registering the administrator, see page 14
"Registering and Changing Administrators".
You can specify the login user name and password, and encryption password for each administrator.
The encryption password is used for encrypting data transmitted via SNMPv3. It is also used by
applications such as Device Manager NX that use SNMPv3. Administrators can only manage the
machine's settings and control user access, Administrators can only manage the machine's settings and
control user access; they cannot use functions such as printing documents. To use this function, the
administrator must register as a user in the Address Book, and then be authenticated. Specify
administrator authentication, and then specify user authentication. For details about specifying
authentication, see page 25 "Configuring User Authentication".
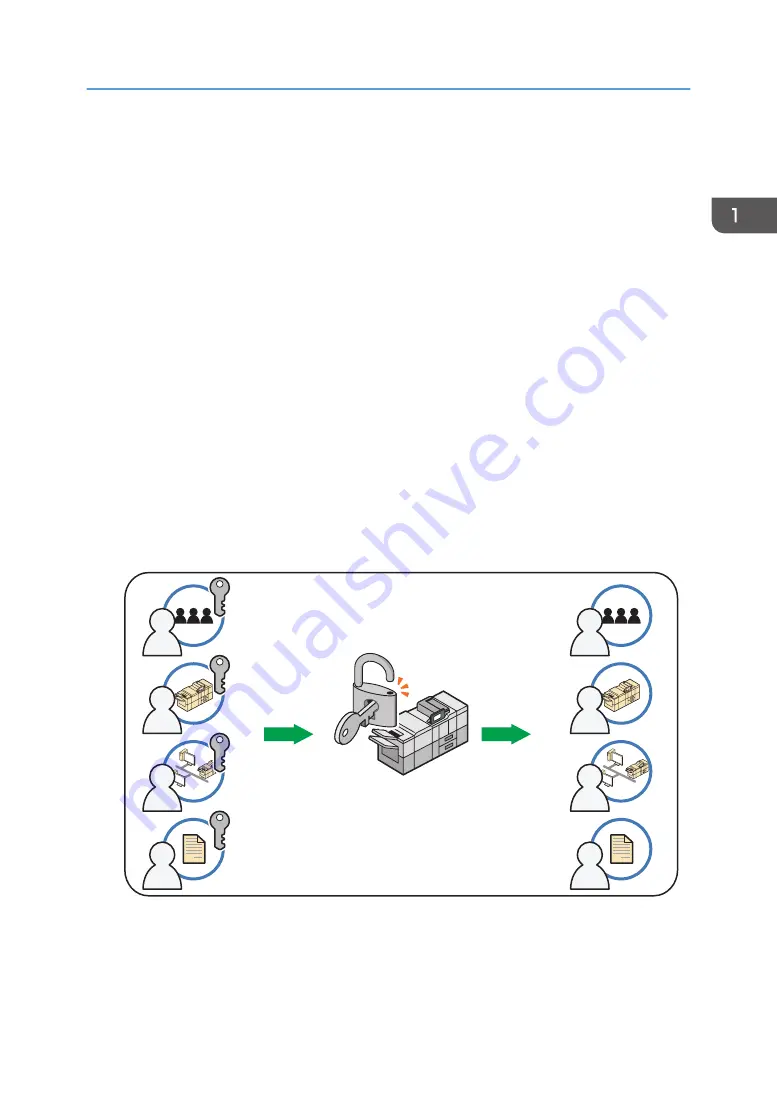
Roles of each administrator
1
2
3
4
CZB009
1. User administrator
Manages personal information in the Address Book.
A user administrator can register/delete users in the Address Book or change users' personal
information.
Configuring Administrator Authentication
11
Summary of Contents for PRO C9100
Page 2: ......
Page 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Page 24: ...1 Getting Started 22...
Page 72: ...4 Preventing Leakage of Information from Machines 70...
Page 116: ...5 Enhanced Network Security 114...
Page 176: ...6 Managing the Machine 174...
Page 188: ...7 Troubleshooting 186...
Page 235: ......
Page 236: ...EN GB EN US EN AU M238 1022 2014...














































