Authentication Information Stored in the Address Book
If you have enabled user authentication, you can specify access limits and usage limits to the machine's
functions for each user or group of users. Specify the necessary settings in the Address Book entry of
each user. For details about the functions that can be limited, see page 50 "Limiting Available
Functions".
Users must have a registered account in the Address Book in order to use the machine when user
authentication is specified. For details about user registration in the Address Book, see "Registering User
Information", Connecting the Machine/ System Settings.
User authentication can also be specified via Web Image Monitor. For details, see Web Image Monitor
Help.
Specifying Login User Names and Passwords
In "Address Book Management", specify the login user name and password to be used for "User
Authentication Management".
For the characters that can be used for login user names and passwords, see page 15 "Usable
characters for user names and passwords".
1.
Log in as the user administrator from the control panel.
2.
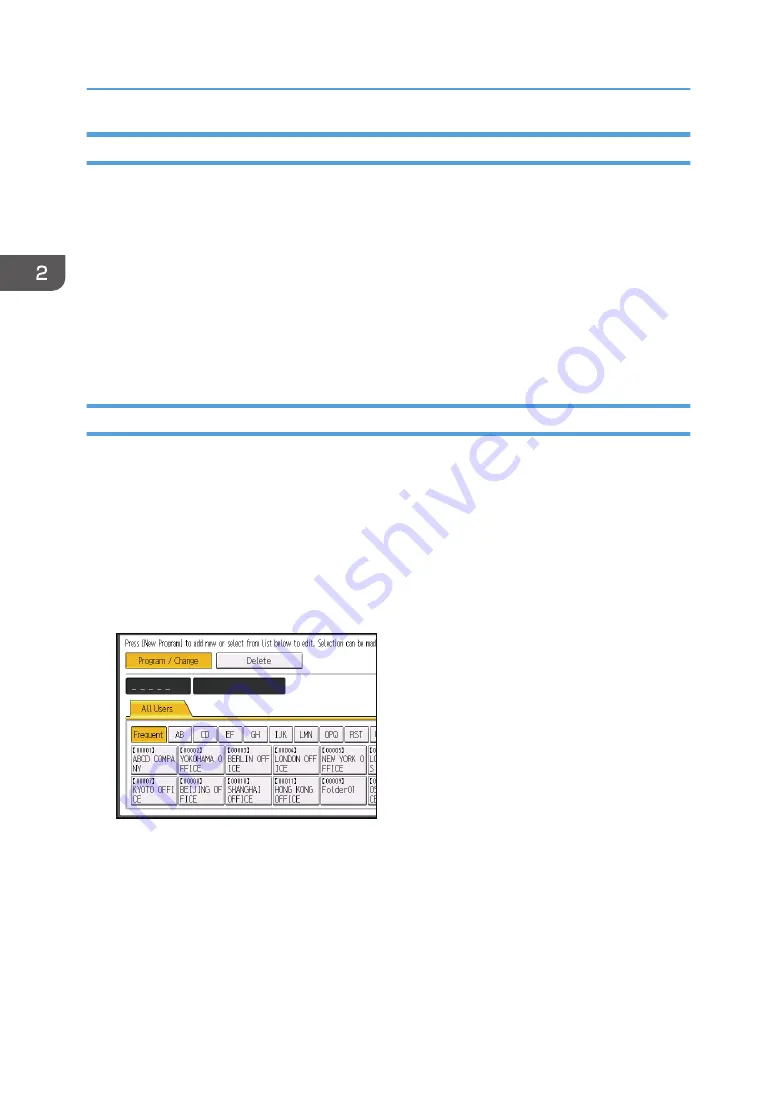
Press [Address Book Mangmnt].
3.
Select the user.
2. Configuring User Authentication
30
Summary of Contents for PRO C9100
Page 2: ......
Page 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Page 24: ...1 Getting Started 22...
Page 72: ...4 Preventing Leakage of Information from Machines 70...
Page 116: ...5 Enhanced Network Security 114...
Page 176: ...6 Managing the Machine 174...
Page 188: ...7 Troubleshooting 186...
Page 235: ......
Page 236: ...EN GB EN US EN AU M238 1022 2014...
















































