Using Web Image Monitor to Manage Log
Files
You can specify the types of log to store on the machine and the log collection level. You can also bulk
delete or download log files.
Logs That Can Be Managed Using Web Image Monitor
The following tables explain the items in the job log and access log that the machine creates when you
enable log collection using Web Image Monitor. If you require log collection, use Web Image Monitor
to configure it. This setting can be specified in [Logs] under [Configuration] in Web Image Monitor.
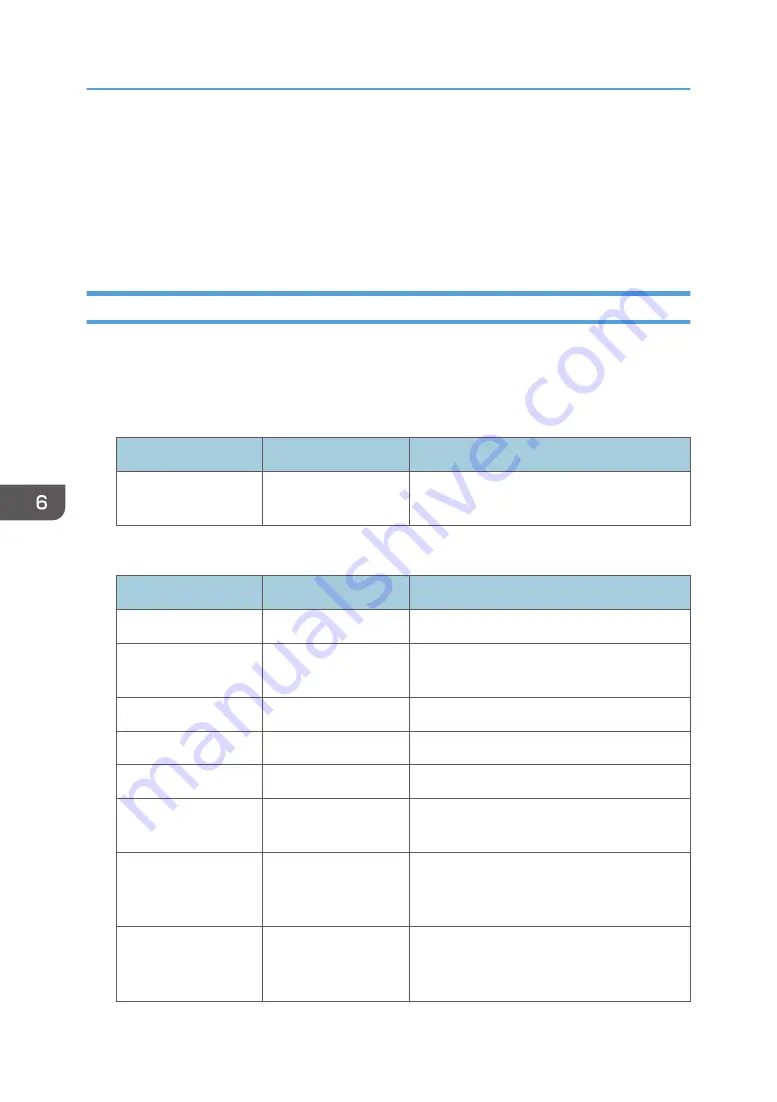
Job log information items
Job Log Item
Log Type Attribute
Content
Report Printing
Report Printing
Details of reports printed from the control
panel.
Access log information items
Access Log Item
Log Type Attribute
Content
Login
Login
Times of login and identity of logged in users.
Logout
Logout
Times of logout and identity of logged out
users.
HDD Format
HDD Format
Details of hard disk formatting.
All Logs Deletion
All Logs Deletion
Details of deletions of all logs.
Log Setting Change
Log Setting Change
Details of changes made to log settings.
Transfer Log Result
Transfer Log Result
Log of the result of log transfer to Remote
Communication Gate S.
Log Collection Item
Change
Log Collection Item
Change
Details of changes to job log collection levels,
access log collection levels, and types of log
collected.
Collect Encrypted
Communication Logs
Collect Encrypted
Communication Logs
Log of encrypted transmissions between the
utility, Web Image Monitor or outside
devices.
6. Managing the Machine
116
Summary of Contents for PRO C9100
Page 2: ......
Page 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Page 24: ...1 Getting Started 22...
Page 72: ...4 Preventing Leakage of Information from Machines 70...
Page 116: ...5 Enhanced Network Security 114...
Page 176: ...6 Managing the Machine 174...
Page 188: ...7 Troubleshooting 186...
Page 235: ......
Page 236: ...EN GB EN US EN AU M238 1022 2014...