S&C Instruction Sheet 1072-530
23
Network Configuration
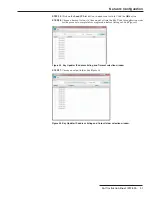
Figure 38. Configuration File MAC Address specification for MAC-specific encryption/
decryption.
Configuration files are always encrypted to prevent tampering with radio configuration
and to prevent snooping radio configurations during configuration uploads. When a keyset
is used to encrypt/decrypt the configuration, the target radio must have that same keyset
loaded to successfully upload and implement the network configuration.
Click on any of the tabs shown in Figure 36 on page 22 to set up the network configu-
ration for the area listed in that tab. Network-configuration functions parallel the corre-
sponding tabs in the SpeedNet Client Tool, but instead of applying to the radio the client
is connected to, the settings developed in the network configuration are saved in a file
that can be uploaded and applied to the corresponding radio by using the client tool’s
Set
Network Configuratio
n function described in the “Security Window, Encryption Tab”
section on page 51.
The network configuration areas are described in Figure 39.
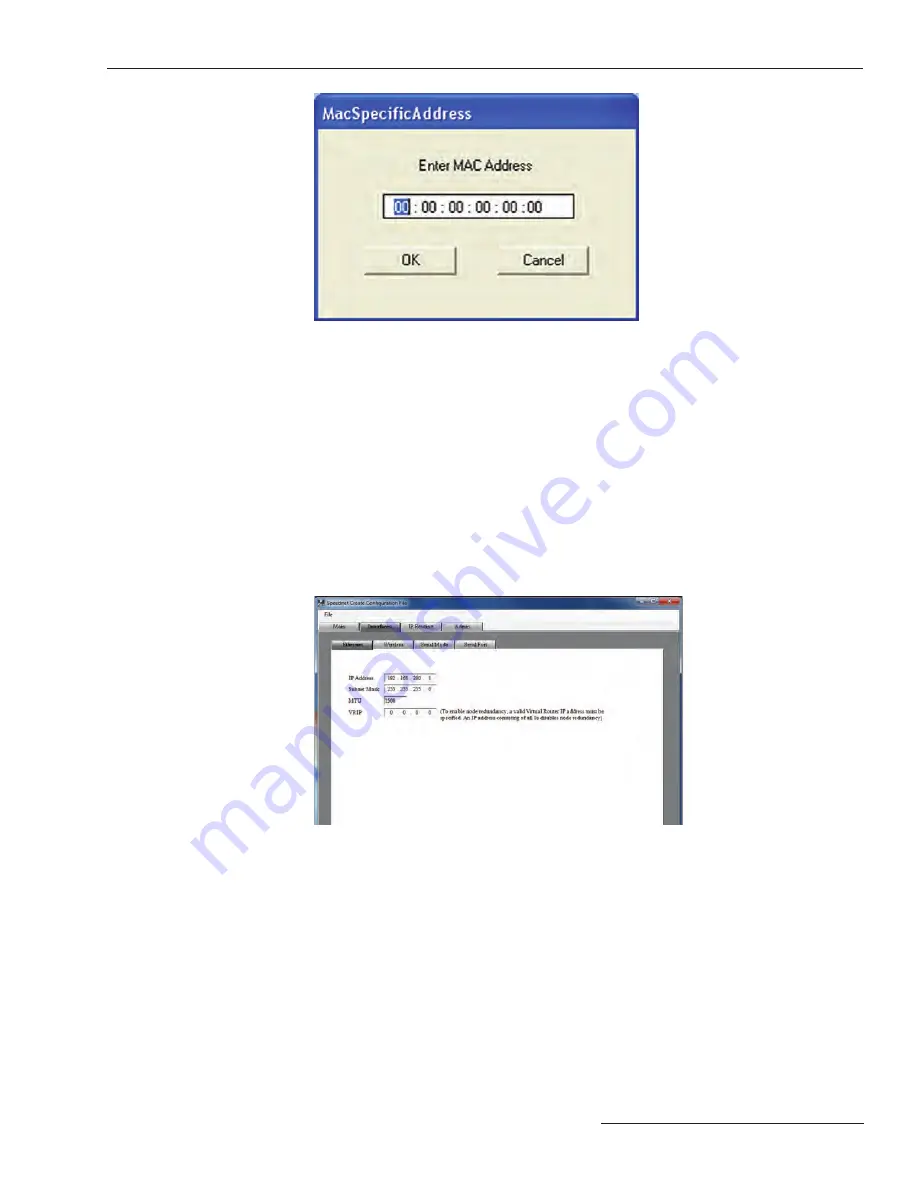
Figure 39. The Network Configuration of Ethernet Interface.
Figure 39 shows the
Network Configuration
window for configuring the Ethernet
Interface. The IP Address, Subnet Mask, MTU, and VRIP settings function the same as in
the corresponding
SpeedNet Client
window as described in the “Interfaces Window,
Ethernet Tab” section starting on page 35. There is no
Apply
button on this window
because application to a radio is deferred until uploaded using the SpeedNet Client tool.
Please note that on a given SpeedNet Radio mesh, the configurations of all the Ether-
net interfaces should differ so there is no overlap between the Ethernet port subnets or
between the Ethernet port subnets and the wireless subnet.