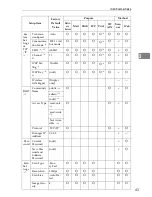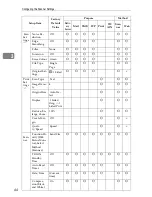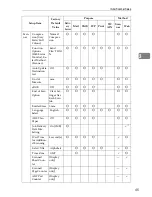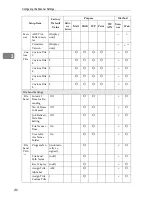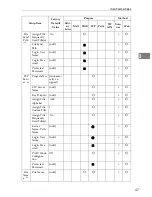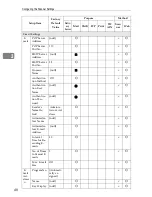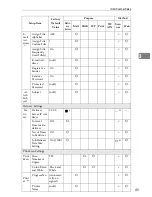
System Settings
53
3
❖
❖
❖
❖
Subnet Mask
When a fixed IP address is as-
signed to this machine on the net-
work you use, enter the subnet
mask to this item in the form of
xxx.xxx.xxx.xxx (xxx:0 through
255).
Do not specify this item manually
when you use this machine on a
DHCP environment, because this
item is automatically assigned to
this machine by selecting " DHCP "
for
[
Network Boot
]
.
❖
❖
❖
❖
Default Gateway Address
When a fixed IP address is as-
signed to this machine on the net-
work you use, enter the default
gateway address to this item in the
form of xxx.xxx.xxx.xxx (xxx:0
through 255).
Do not specify this item manually
when you use this machine on a
DHCP environment, because this
item is automatically assigned to
this machine by selecting " DHCP "
for
[
Network Boot
]
.
❖
❖
❖
❖
Access Control and Access Mask
Use these setup items together to
determine which of client comput-
ers has right to access this machine
w h e n i t w o r k s a s a n e t w o r k
TWAIN scanner.
Each of the client computers is
granted or denied its access to this
machine by its IP address, which is
determined by an access control
entry and an access mask entry in
combination. An access control en-
try is used as a reference value of
the IP address, while an access
mask entry determines the range
of the IP addresses.
• Access control is the value that
becomes the reference for re-
stricting the client that uses this
product as a network TWAIN
scanner
• Access mask is the value to
specify the restriction range. It
is collated (logically multiplied)
with access control to limit cli-
ents that can use this product as
a network TWAIN scanner.
Specify both the access control and
the access mask in the form of
xxx.xxx.xxx.xxx (xxx:0 through
255).
Note
❒
When you want to set no limita-
tion of access to this machine,
leave these settings as their de-
fault values.
❒
When an IP address of a client
computer falls within the logi-
cal products of the access con-
trol entry and the access mask
entry, the client computer is
granted its access to this ma-
chine.
❒
For example, a client computer
that has an IP address within
the range shown under “Ac-
cess-enabled IP address” col-
umn in the following table has
right to access this machine, in
accordance with the entry of the
access mask to the left, when
you set the access control to
192.168.15.18. In the following
table, “xxx” means any value is
available.
Access mask en-
try
Access-enabled
IP address
000.000.000.000
xxx.xxx.xxx.xxx
255.255.000.000
192.168.xxx.xxx
255.255.240.000
192.168.0.xxx
∼
192.168.15.xxx
255.255.255.000
192.168.15.xxx
255.255.255.240
192.168.15.16
∼
192.168.15.31
255.255.255.255
192.168.15.18
Summary of Contents for IS300e
Page 8: ...vi...
Page 14: ...6...
Page 30: ...What You Can Do With This Machine 22 1...
Page 116: ...Configuring the Scanner Settings 108 3...
Page 126: ...Setting Originals 118 4...
Page 146: ...Sending Scan File by E mail 138 6...
Page 162: ...Sending Scan File by Scan to FTP 154 8...
Page 166: ...Sending Scan Files Using Delivery Server 158 9...
Page 176: ...Printing Scanned Image Files 168 10...
Page 204: ...Appendix 196 11 When Gray scale is selected...
Page 206: ...Appendix 198 11 When 256 colors is selected...
Page 222: ...Image Scanner Operating Instructions GB GB G421 8601...