Copyright (c) 2000-2009 Acronis. All rights reserved.
Copyright (c) 2009 Seagate Technology LLC. All Rights Reserved. 41
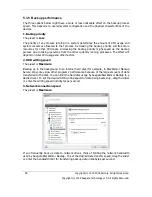
5.3.11 Creating a custom data category for backups
To add a custom data category, click
Create
in the
Choose files to back up
screen of the
Backup Wizard, select the folder (data source) and provide a name for the category. You can
include in the category all files in the selected folder or apply filters to select the specific
types of files that you wish or do not wish to back up.
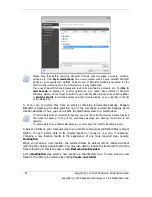
To set a filter, select its type:
Back up files of the following types only
or
Back up files
of all types in the source except the following
. Then click
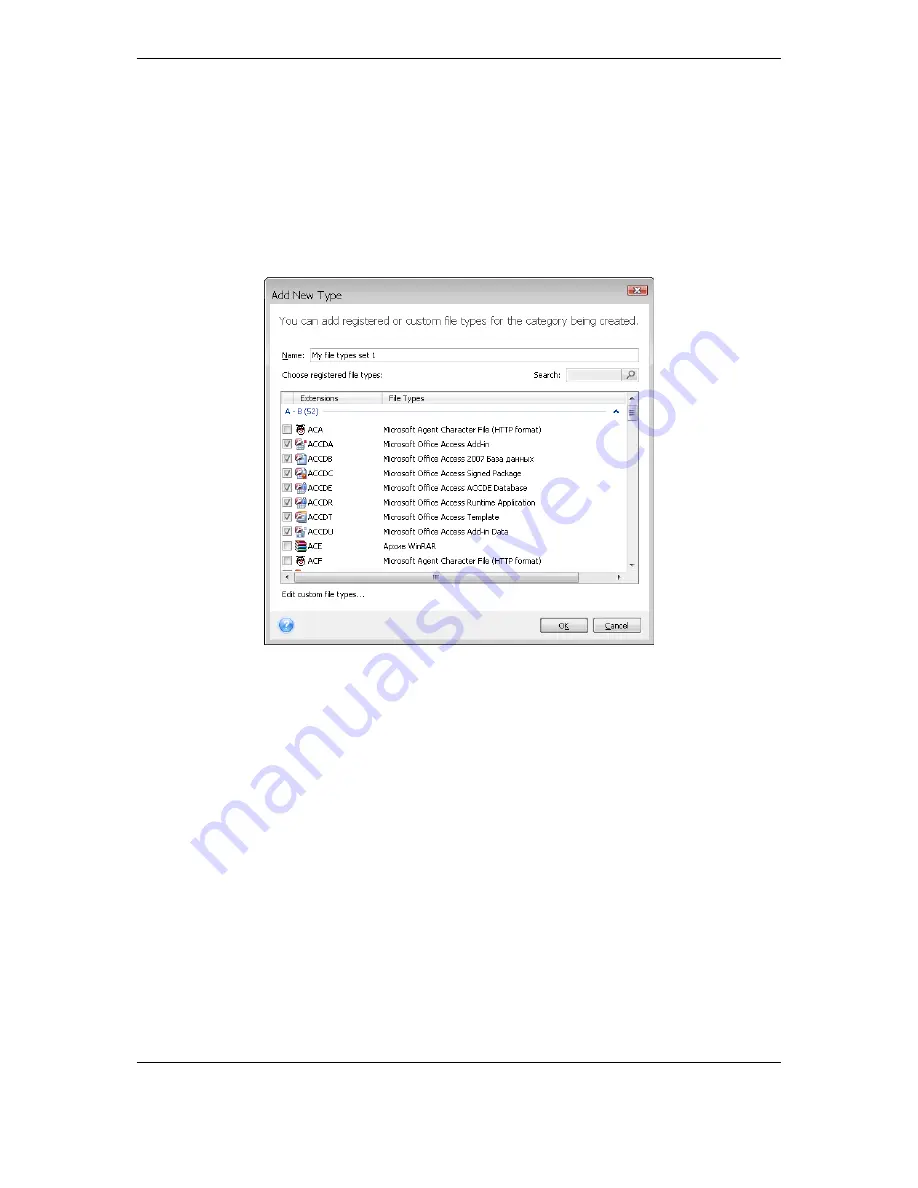
Add new
and select the
desired file types in the window that appears.
You can select file types as follows:
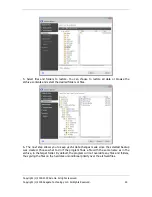
1. By name. Enter the file name in the upper
Name
field. You can use the common
Windows wildcard characters. For example,
My???.exe
will select all .exe files with names
consisting of five symbols and starting with ―my‖.
2. By type. Select the desired file types in the list. You can also search desired registered file
types by entering their extension or description in the
Search
field.
3. By extension. Click the
Edit custom file types…
link and enter the extensions
(semicolon separated) in the
File extensions
field.
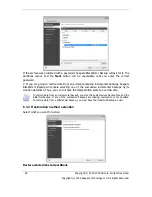
If you do not want to keep custom contents of the current backup, simply select the
files/folders from the tree. This set will be effective only for the current backup task.
5.4 Making reserve copies of your backups
When you choose the My Data backup type for backing up selected files and folders, you can
create reserve copies of your backups and save them on the Seagate NAS or Seagate DAS
devices.
You have a choice of making a reserve copy in the form of regular files, a zip compressed
file, or a tib file (optionally with password protection and encryption).
Summary of Contents for BlackArmor NAS 110
Page 1: ......