12 Menu Extras
Securepoint 10
Securepoint
Security Solutions
181
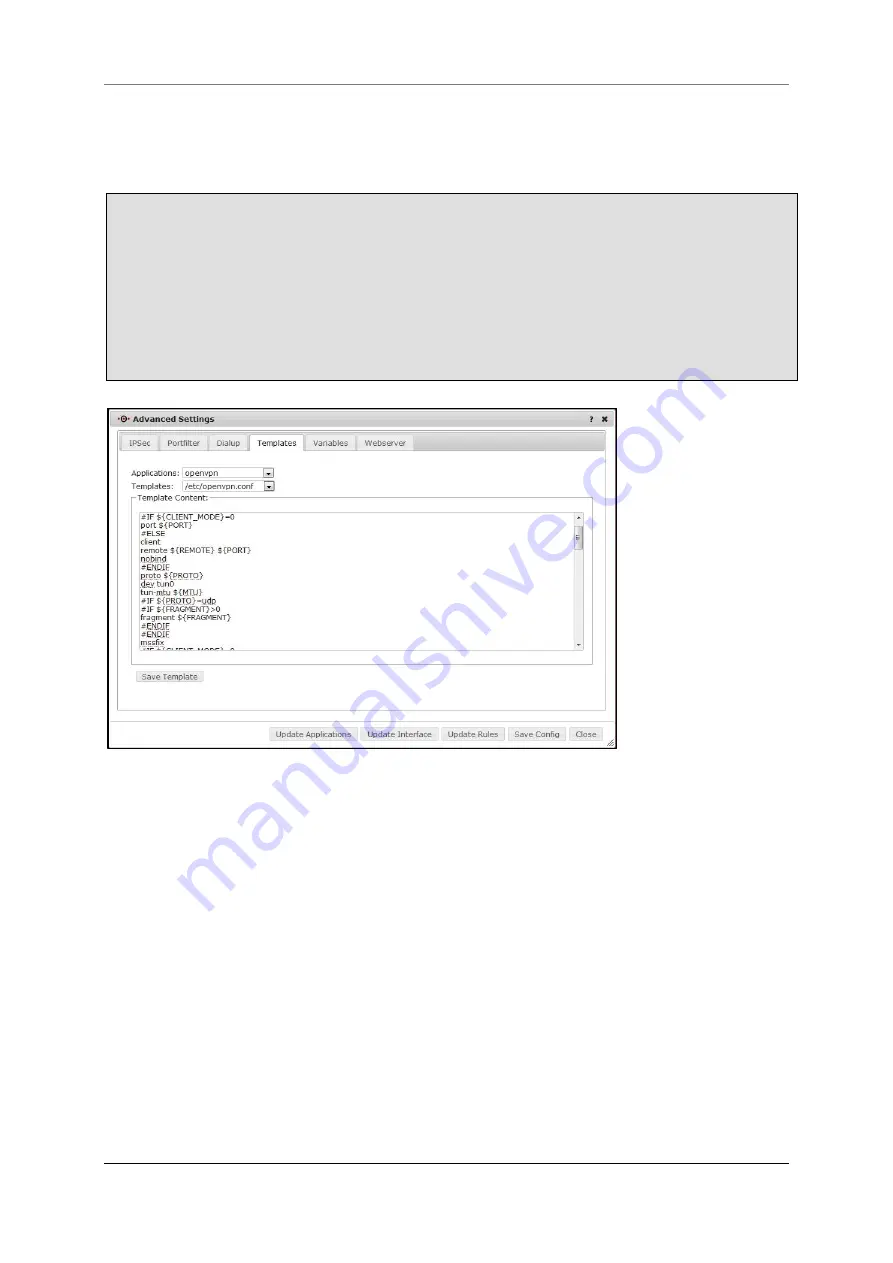
12.6.5 Templates
On this tab you can edit all templates on the firewall.
Select the application you want to edit from the dropdown list
Applications
.
The firewall displays the depending templates in the dropdown field
Templates
.
Select the template you want to edit from the dropdown box
Templates
.
The template will be displayed in the section
Template Content
.
Adjust the template for your needs.
Store the changes with
Save Template
.
For applying the changes immediately click the button
Update Applications
.
fig. 198 edit template







































