Security recommendations
3
NOTICE
Information security
Connect to the device and change the standard passwords for the users "admin" and "user"
before you operate the device. To be able to change passwords you need to be logged in with
write access to the configuration data.
To prevent unauthorized access to the device and/or network, observe the following security
recommendations.
General
• Check the device regularly to ensure that these recommendations and/or other internal
security policies are complied with.
• Evaluate the security of your location and use a cell protection concept with suitable products
https://www.industry.siemens.com/topics/global/en/industrial-security/Seiten/
• When the internal and external network are disconnected, an attacker cannot access internal
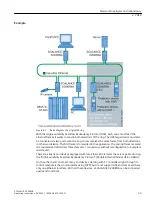
data from the outside. Therefore operate the device only within a protected network area.
• No product liability will be accepted for operation in a non-secure infrastructure.
• Use VPN to encrypt and authenticate communication from and to the devices.
• For data transmission via a non-secure network, use an encrypted VPN tunnel (IPsec,
OpenVPN).
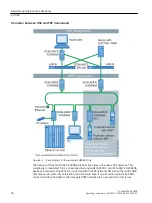
• Separate connections correctly (WBM, SSH etc.).
• Check the user documentation of other Siemens products that are used together with the
device for additional security recommendations.
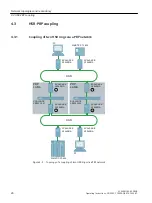
• Using remote logging, ensure that the system protocols are forwarded to a central logging
server. Make sure that the server is within the protected network and check the protocols
regularly for potential security violations or vulnerabilities.
Physical access
• Restrict physical access to the device to qualified personnel because the plug-in data medium
can contain sensitive data.
• Lock unused physical interfaces on the device. Unused interfaces can be used to gain access
to the plant without permission.
SCALANCE X-200RNA
Operating Instructions, 04/2022, C79000-G8976-C342-07
15