RUGGEDCOM ROS
User Guide
Chapter 6
Troubleshooting
General
247
Troubleshooting
This chapter describes troubleshooting steps for common issues that may be encountered when using
RUGGEDCOM ROS or designing a network.
IMPORTANT!
For further assistance, contact a Customer Service representative.
CONTENTS
•
•
•
•
Section 6.1
General
The following describes common problems.
Problem
Solution
The switch is not responding to ping
attempts, even though the IP address and
gateway have been configured. The switch
is receiving the ping because the LEDs are
flashing and the device statistics are logging
the pings. What is going on?
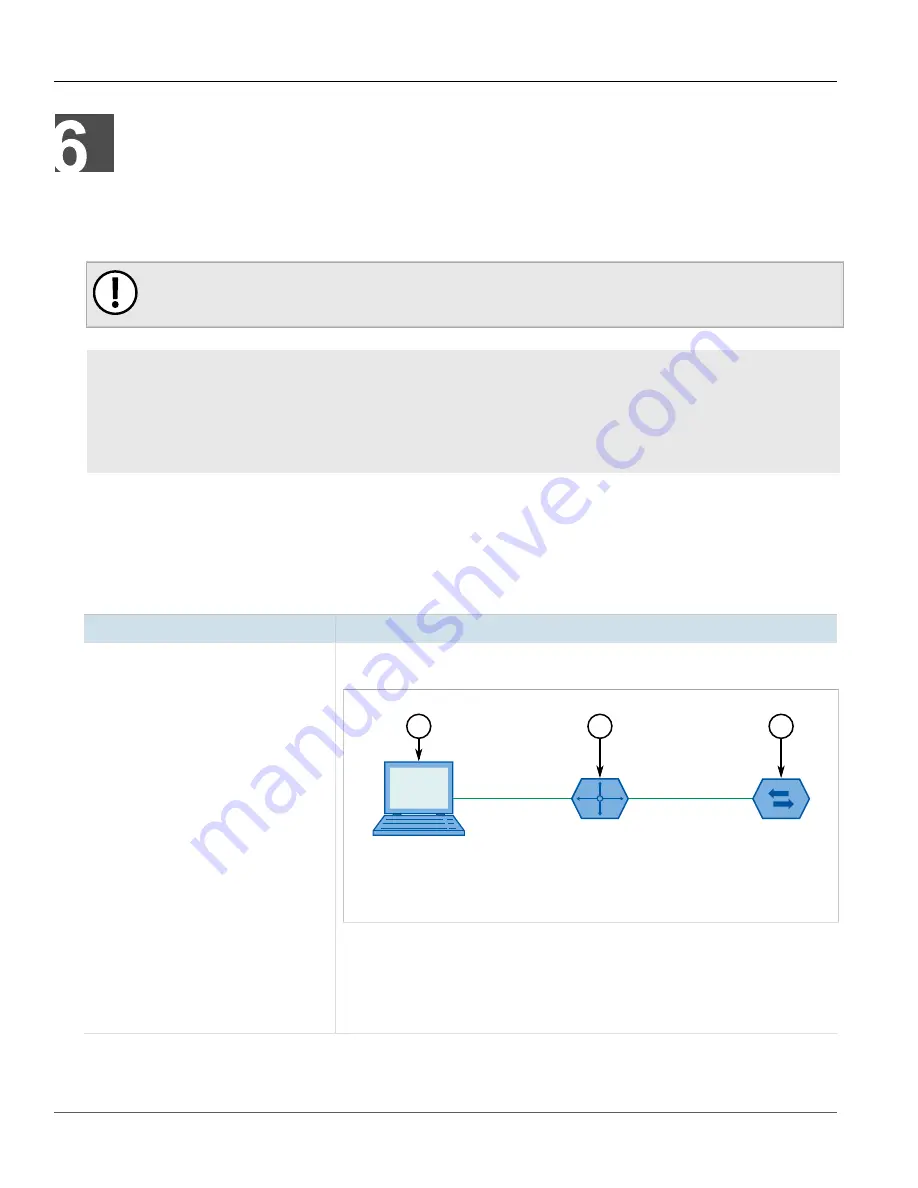
Is the switch being pinged through a router? If so, the switch gateway address must be
configured as well. The following figure illustrates the problem.
192.168.0.2
192.168.0.1
10.10.0.1
10.10.0.2
1
2
3
Figure 177: Using a Router As a Gateway
1.
Work Station
2.
Router
3.
Switch
The router is configured with the appropriate IP subnets and will forward the ping from the
workstation to the switch. When the switch responds, however, it will not know which of its
interfaces to use in order to reach the workstation and will drop the response. Programming
a gateway of 10.0.0.1 will cause the switch to forward unresolvable frames to the router.
This problem will also occur if the gateway address is not configured and the switch tries to
raise an SNMP trap to a host that is not on the local subnet.