Chapter 5
Setup and Configuration
RUGGEDCOM ROS
User Guide
234
IEEE 802.1X Authentication with MAC Address-Based
Authentication
4
3
2
1
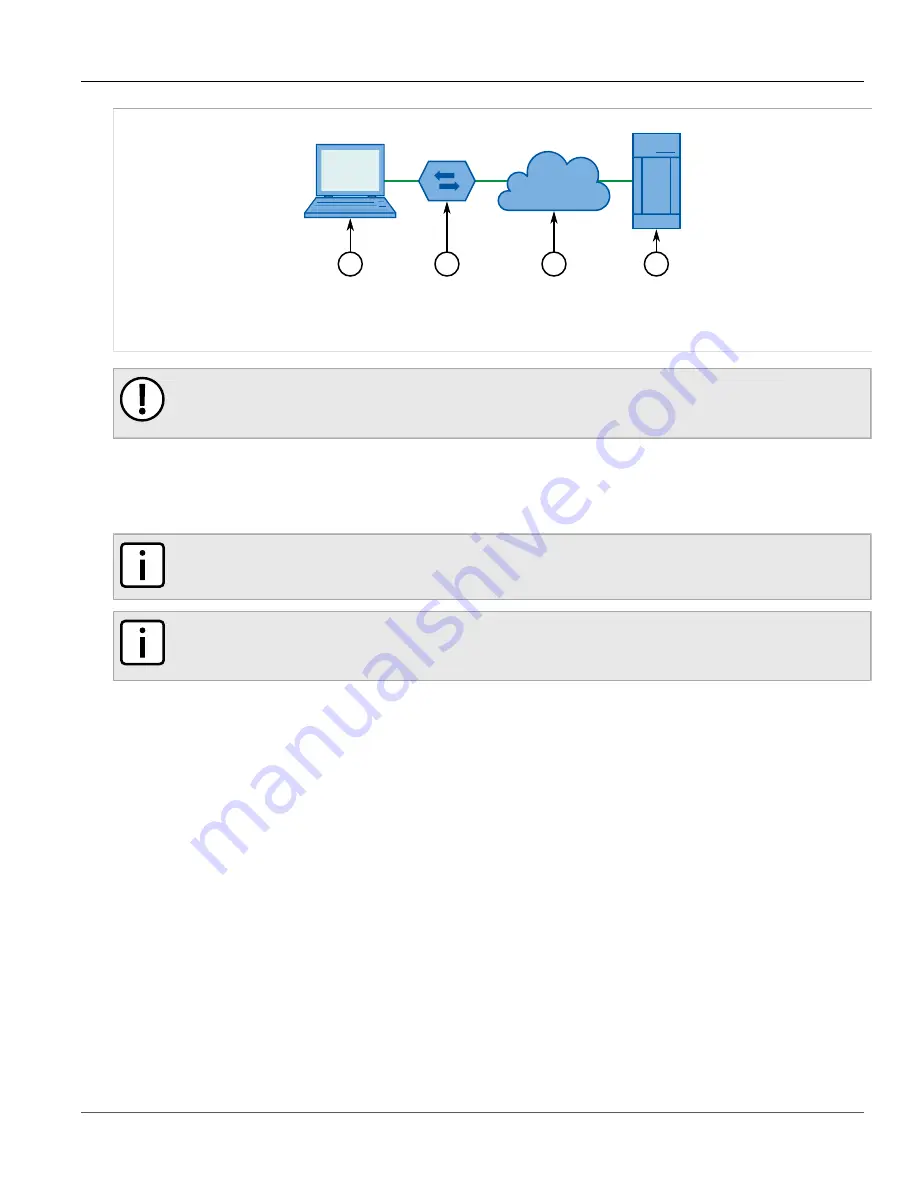
Figure 165: IEEE 802.1x General Topology
1.
Supplicant
2.
Authenticator Switch
3.
LAN
4.
Authentication Server
IMPORTANT!
RUGGEDCOM ROS supports both Protected Extensible Authentication Protocol (PEAP) and EAP-MD5.
PEAP is more secure and is recommended if available in the supplicant.
IEEE 802.1x makes use of the Extensible Authentication Protocol (EAP), which is a generic PPP authentication
protocol that supports various authentication methods. IEEE 802.1x defines a protocol for communication
between the Supplicant and the Authenticator, referred to as EAP over LAN (EAPOL).
RUGGEDCOM ROS communicates with the Authentication Server using EAP over RADIUS.
NOTE
The switch supports authentication of one host per port.
NOTE
If the host’s MAC address is configured in the Static MAC Address Table, it will be authorized, even if the
host authentication is rejected by the authentication server.
Section 5.9.1.3
IEEE 802.1X Authentication with MAC Address-Based Authentication
This method, also referred to as MAB (MAC-Authentication Bypass), is commonly used for devices, such as VoIP
phones and Ethernet printers, that do not support the 802.1x protocol. This method allows such devices to be
authenticated using the same database infrastructure as that used in 802.1x.
IEEE 802.1x with MAC-Authentication Bypass works as follows:
1. The device connects to a switch port.
2. The switch learns the device MAC address upon receiving the first frame from the device (the device usually
sends out a DHCP request message when first connected).
3. The switch sends an EAP Request message to the device, attempting to start 802.1X authentication.
4. The switch times out while waiting for the EAP reply, because the device does not support 802.1x.
5. The switch sends an authentication message to the authentication server, using the device MAC address as
the username and password.
6. The switch authenticates or rejects the device according to the reply from the authentication server.