RUGGEDCOM WIN
User Guide
Chapter 3
Device Management
Copying Files to the Secondary Bank
31
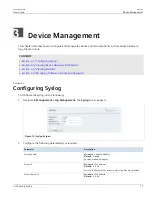
Figure 24: Secondary Components Screen
2. Select a file from the table.
3. Click
Upload File
.
4. View the status of the operation. For more information, refer to
Section 3.4.8, “Viewing the Status of an
.
Section 3.4.7.3
Copying Files to the Secondary Bank
To copy files to the secondary bank, do the following:
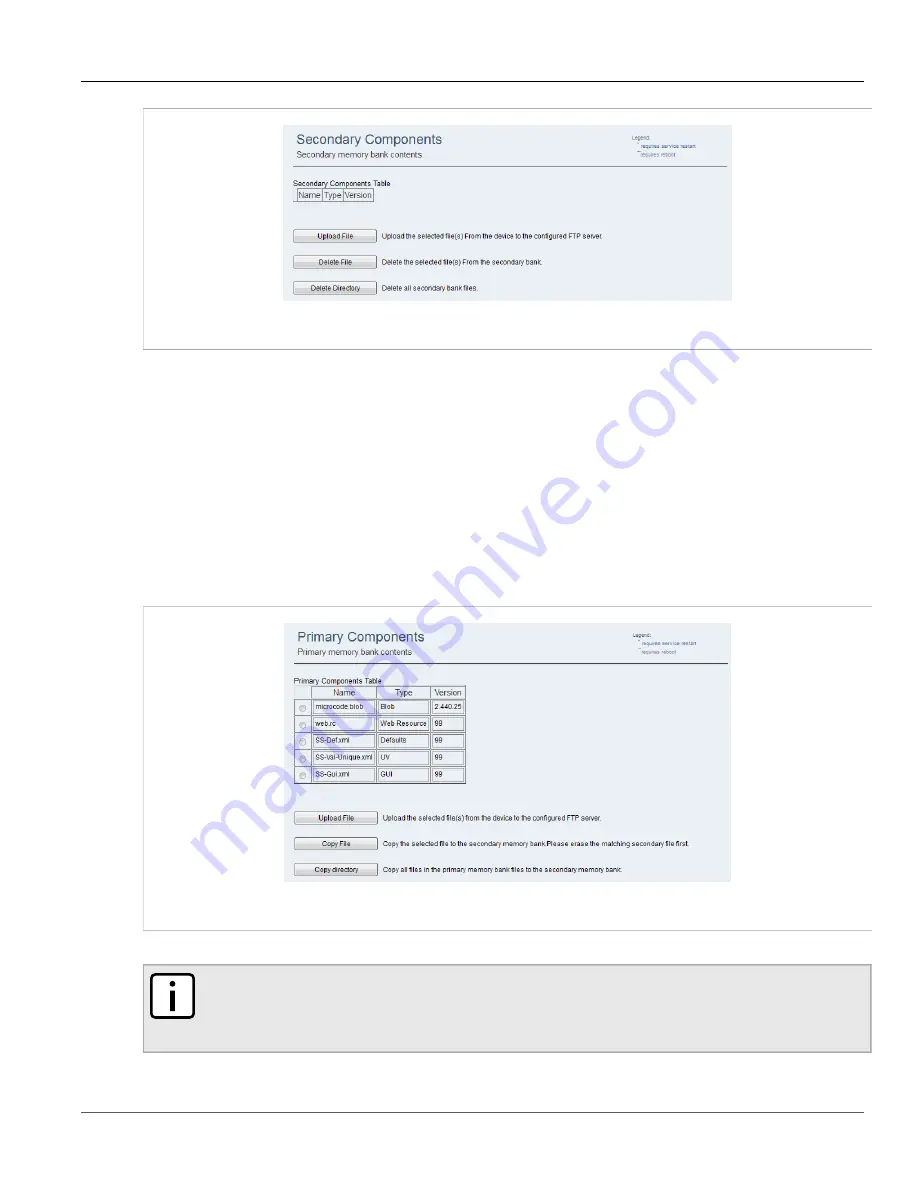
1. Navigate to
Management » SW Upgrade » Primary Bank
. The
Primary Components
screen appears.
Figure 25: Primary Components Screen
2. Select a file from the table.
NOTE
Before copying the file, make sure it does not already exist in the Secondary memory bank. If the
file is present in the Secondary memory bank, delete the file from the Secondary memory bank
before copying. For more information, refer to
Section 3.4.7.4, “Deleting Memory Bank Files”
.