RUGGEDCOM WIN
User Guide
Chapter 5
Setup and Configuration
Configuring the Network Interface Protocol (NIP)
69
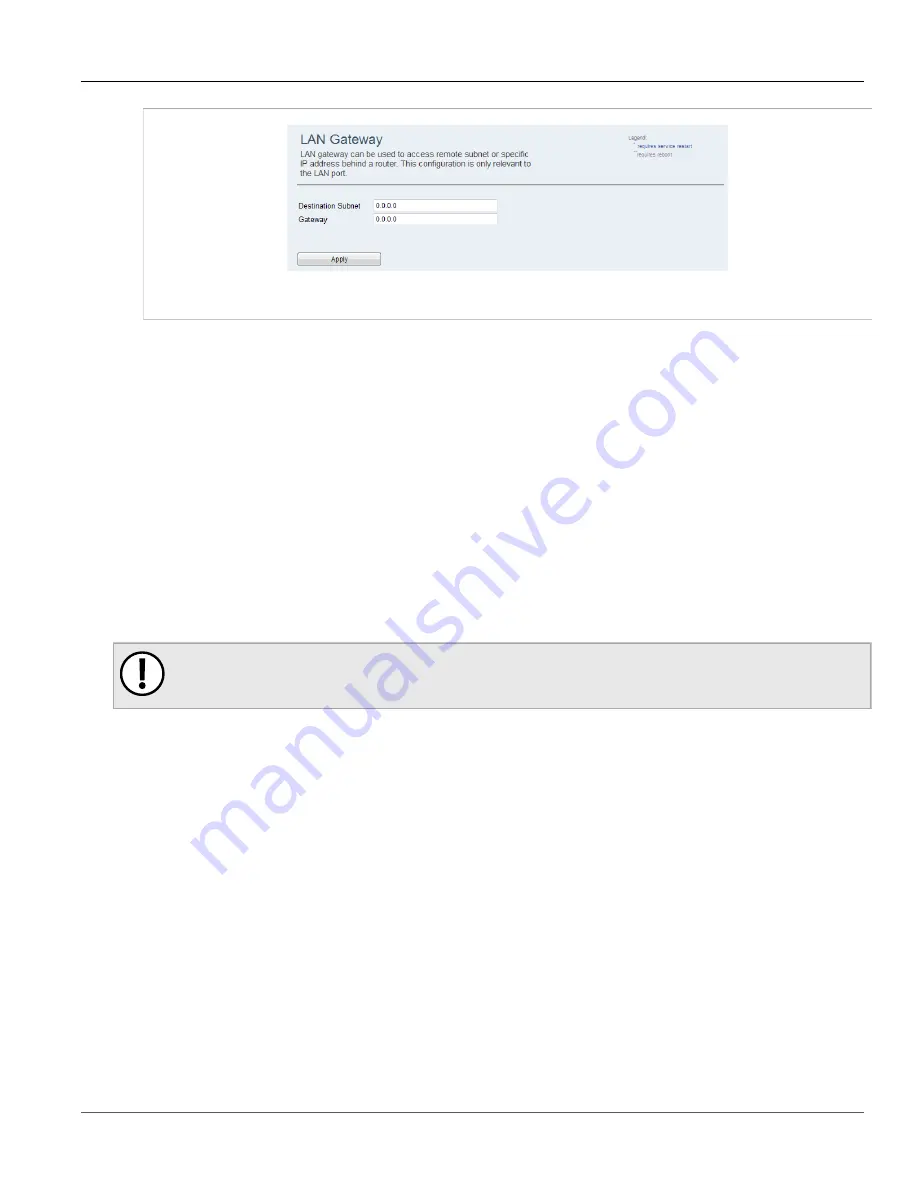
Figure 62: LAN Gateway Screen
2. In the
Destination Subnet
parameter, type the IP address for the destination subnet.
3. In the
Gateway
parameter, type the IP address for the gateway.
4. Click
Apply
.
Section 5.10
Configuring the Network Interface Protocol (NIP)
The Network Interface Protocol (NIP) is a software module of the RUGGEDCOM WIN firmware designed to allow
third party applications, such as management and control systems, to query the device with relatively high speed
and efficiency. Details about this application programming interface (API) can be provided upon request.
NIP can be enabled or disabled and the UDP port can be changed.
For more information about interfacing with the device using NIP, refer to the FAQ
[http://support.automation.siemens.com/WW/view/en/109741871]
.
IMPORTANT!
Only users with Admin access rights can change the NIP settings.
To configure NIP, do the following:
1. Navigate to
Management » NIP
. The
Network Interface Protocol
screen appears.