Safety instructions
2.3 Protocols
Mobile reader SIMATIC RF360M/RF660M
Operating Instructions, 08/2022, C79000-G8976-C660-02
11
2.3
Protocols
Secure/non-secure protocols
•
Use only secure protocols when access to the device is not secured by physical protection
measures.
The following protocols provide secure alternatives:
HTTP
→
HTTPS
•
To prevent unauthorized access to the device or network, set up appropriate safeguards
against non-secure protocols.
•
Enable only the services (protocols) that will actually be used on the device. The same
applies to the installed interfaces/ports. Unused ports could be used to access the network
downstream from the device.
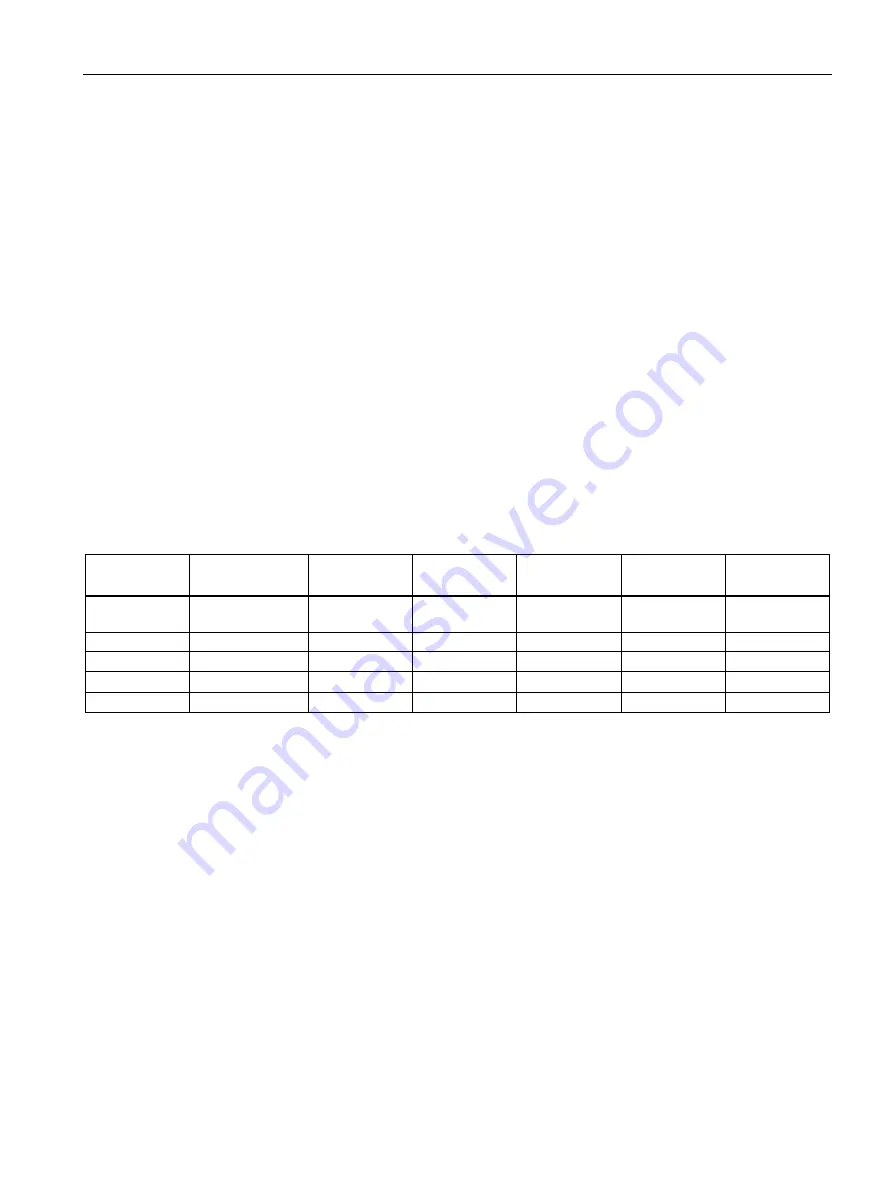
List of available protocols
All available protocols and their ports that are used with SIMATIC RF160B are listed below.
Table 2- 1
List of available protocols
Service/
Protocol
Protocol/
Port number
Preset port
status
Port
configurable
Port number
configurable
Authenticatio
n
Encryption
1)
DHCP
UDP/67
UDP/68
Open
✓
--
--
--
NTP
UDP/123
Open
✓
--
--
--
DNS
UDP/53
Open
✓
--
--
--
HTTP
TCP/80
Open
2)
✓
--
--
--
HTTPS
TCP/443
Open
2)
✓
--
--
✓
1)
You can find more information on the encryption methods used in the appendix.
2)
If the application was started.
Explanation of the table:
•
Authentication
Specifies whether authentication of the communication partner takes place.
•
Encryption
Specifies whether the transfer is encrypted.












































