Application Examples
6.5 Example of an application "Testing and setting parameters for industrial UHF algorithms"
SIMATIC RF-DIAG
76
Operating Manual, 09/2012, C79000-G8976-C292-01
3.
Set the parameters for Read Boost /Write Boost and optimize them if the inventories are
very successful but the reads and writes are less reliable.
4.
Set parameters for the Black List filter and optimize them.
5.
Decide whether parameter assignment and optimization of inventories should be filtered
using Smoothing or ITF so that these can then have parameters assigned and be
optimized.
6.
Decide whether single tag mode or Intelligent Singletag Mode (ISTM) and Sorting are
necessary to be able to assign parameters and optimize ISTM later.
7.
Decide whether Tag Hold should also be activated if the inventories return good tag
identification but subsequent reads and writes are less often successful and a
permanently set Read Boost /Write Boost with the required power increase leads to too
much interference in the plant.
Since all algorithms are dependent on each other, steps 1 to 7 may need to be worked
through several times.
For multitag mode:
1.
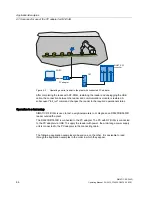
Optimize the antenna configuration (see Example of an application "optimize antenna
position" (Page 67)) including the RSSI Threshold.
2.
Set the parameters for the Power Gap and the Power Ramp and optimize.
3.
Set the parameters for Read Boost /Write Boost and optimize them if the inventories are
very successful but the reads and writes are less reliable.
4.
Set parameters for the Black List filter and optimize them.
Since all algorithms are dependent on each other, steps 1 to 4 may need to be worked
through several times.
If the parameter assignment for the setup was selected suitably, the suitable power will be
selected by the algorithm in an adequately short time to be able to take inventories of the
transponders. The transponders that cannot be identified are discarded by the RSSI filter.
Read and write access is always to the required transponder with the required Read/Write
Boost or Tag Hold.
Possible error symptoms and how to counter them
The possible error symptoms result from the data access statistics of each separate step (1
to 7) achieved for the application. The countermeasures for each error are listed for steps 1
and 2.
For each of the steps 3 to 7, the countermeasure is to set the parameters of each parameter
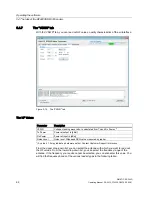
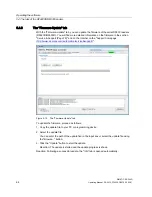
set and optimize them. You are supported by a log file and the "Tag List" tab allowing you to
evaluate the parameter assignment of all the parameters.