Glossary
SINAUT MD741-1
C79000-G8976-C236-05
139
Asymmetrical
encryption
In asymmetrical encryption, data are encrypted with one key and
decrypted with a second key. Both keys are suitable for encryption and
decryption. One of the keys is kept secret by its owner (Private Key),
the other is issued to the public (Public Key), i.e. possible
communication partners.
A message encrypted with a Public Key can only be decrypted and
read by the recipient who has the corresponding Private Key. A
message encrypted with the Private Key can be decrypted by any
recipient who has the corresponding Public Key. Encryption with the
Private Key shows that the message actually originates from the owner
of the corresponding Public Key. We therefore speak of a digital
signature.
Asymmetrical encryption methods such as RSA are, however, slow
and vulnerable to certain attacks, which is why they are often
combined with a symmetrical method (
symmetrical encryption). On
the other hand, concepts are also possible which avoid the complex
administration of symmetrical keys.
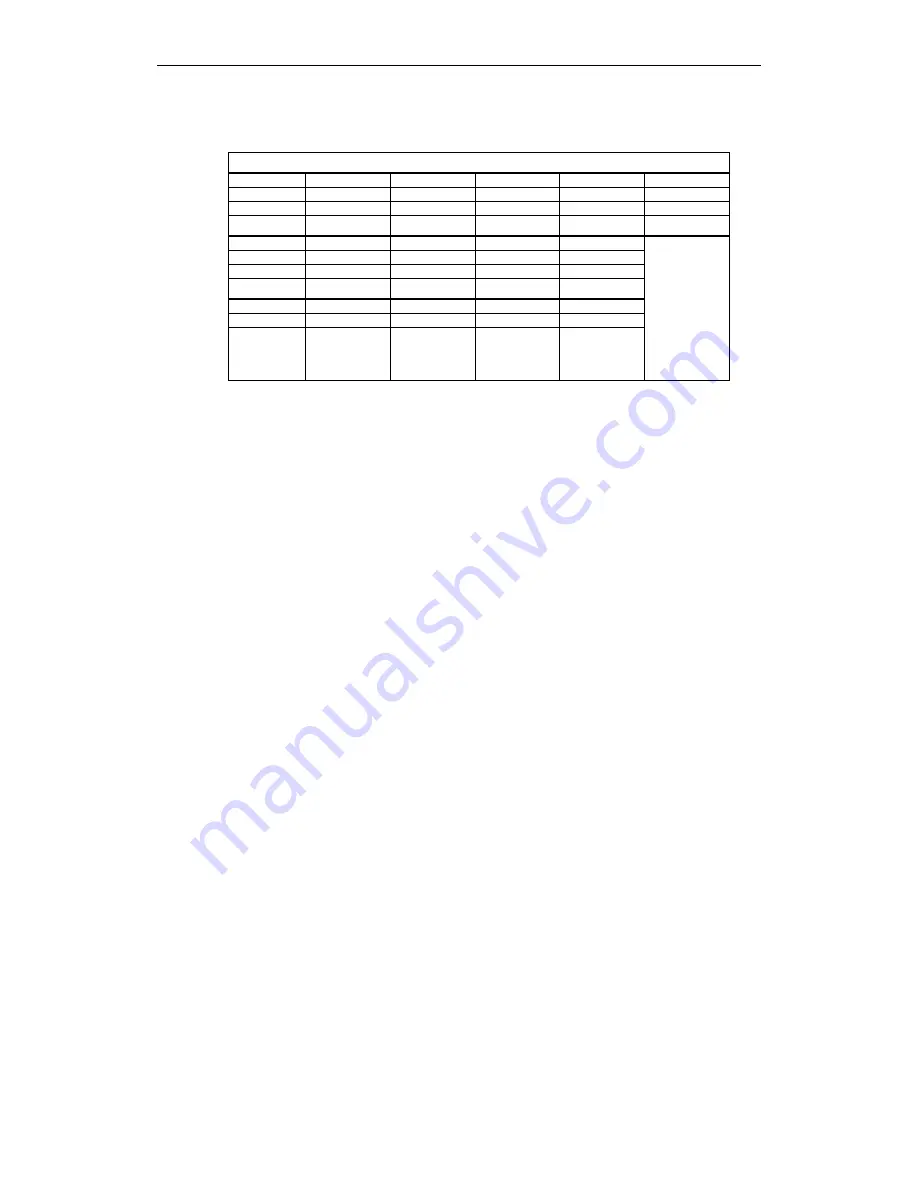
Network A
Computer
A1 A2 A3 A4 A5
IP address
192.168.11.3
192.168.11.4
192.168.11.5
192.168.11.6 192.168.11.7
Network
mask
255.255.255.0 255.255.255.0 255.255.255.0 255.255.255.0 255.255.255.0
Network B
Computer
B1 B2 B3 B4
IP
address 192.168.15.3 192.168.15.4 192.168.15.5 192.168.15.6
Network
mask
255.255.255.0 255.255.255.0 255.255.255.0 255.255.255.0
Network C
Computer
C1 C2 C3 C4
IP
address 192.168.27.3 192.168.27.4 192.168.27.5 192.168.27.6
Network
mask
255.255.255.0 255.255.255.0 255.255.255.0 255.255.255.0
Additional
internal
routes:
Network:
192.168.15.0/24
Gateway:
192.168.11.2
Network:
192.168.27.0/24
Gateway:
192.168.11.2












































