C
ONFIGURING
THE
B
ARRICADE
4-44
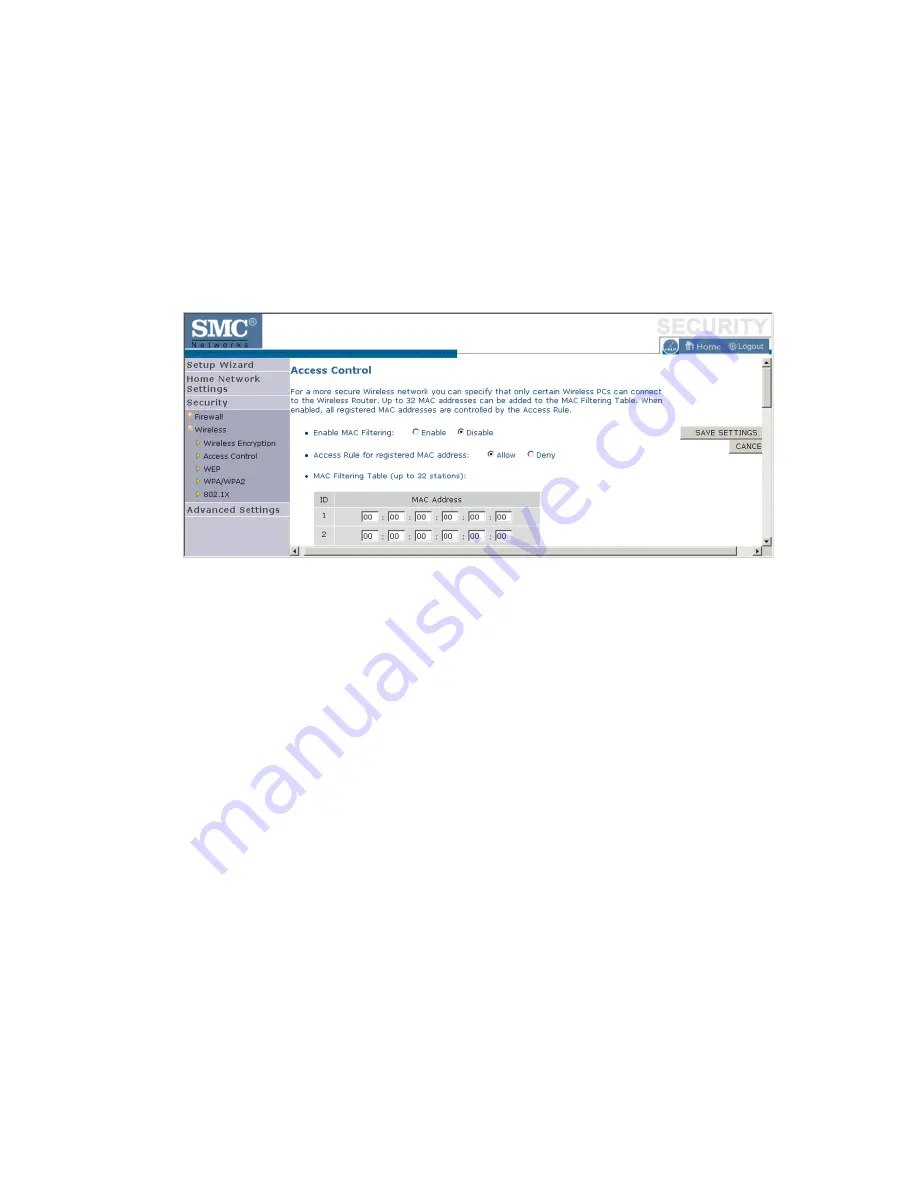
Access Control
For a more secure wireless network you can specify that only certain
wireless clients can connect to the Barricade. Up to 32 MAC addresses can
be added to the MAC Filtering Table. When enabled, all registered MAC
addresses are controlled by the Access Rule.
By default, this MAC filtering feature is disabled.
Summary of Contents for Barricade SMCWBR14T-G
Page 1: ......
Page 2: ......
Page 16: ...TABLE OF CONTENTS xii ...
Page 30: ...INSTALLATION 2 10 ...
Page 48: ...CONFIGURING YOUR MACINTOSH COMPUTER 3 18 ...
Page 131: ......
Page 132: ......