21
©
SOLIDA SYSTEMS INTERNATIONAL 2017
8. Intrusion Detection and Prevention Rules
8.1 Rule Overview
To protect against intrusion attacks, Solida appliances rely on a rule engine that can perform
deep packet inspection (DPI) of Ethernet packets flowing through the appliance. The DPI engine
can inspect all packets and look for signatures and any combination of data patterns, such as
port scans, OS finger printing and vulnerability scans.
The DPI engine is controlled by detection rules. These rules instruct the DPI engine what to look
for in the packets and what action to take if a pattern match is detected.
Solida provides a set of system rules that includes protection from many types of penetration
attempts. An expert user can also create custom rules. Writing custom rules requires detailed
knowledge of rule writing, and the different types of packets flowing over a network. Such
custom rules can be created using the rule editor in the Solida configuration application. In most
cases it is recommended to use the system rules provided by Solida through the threat feed.
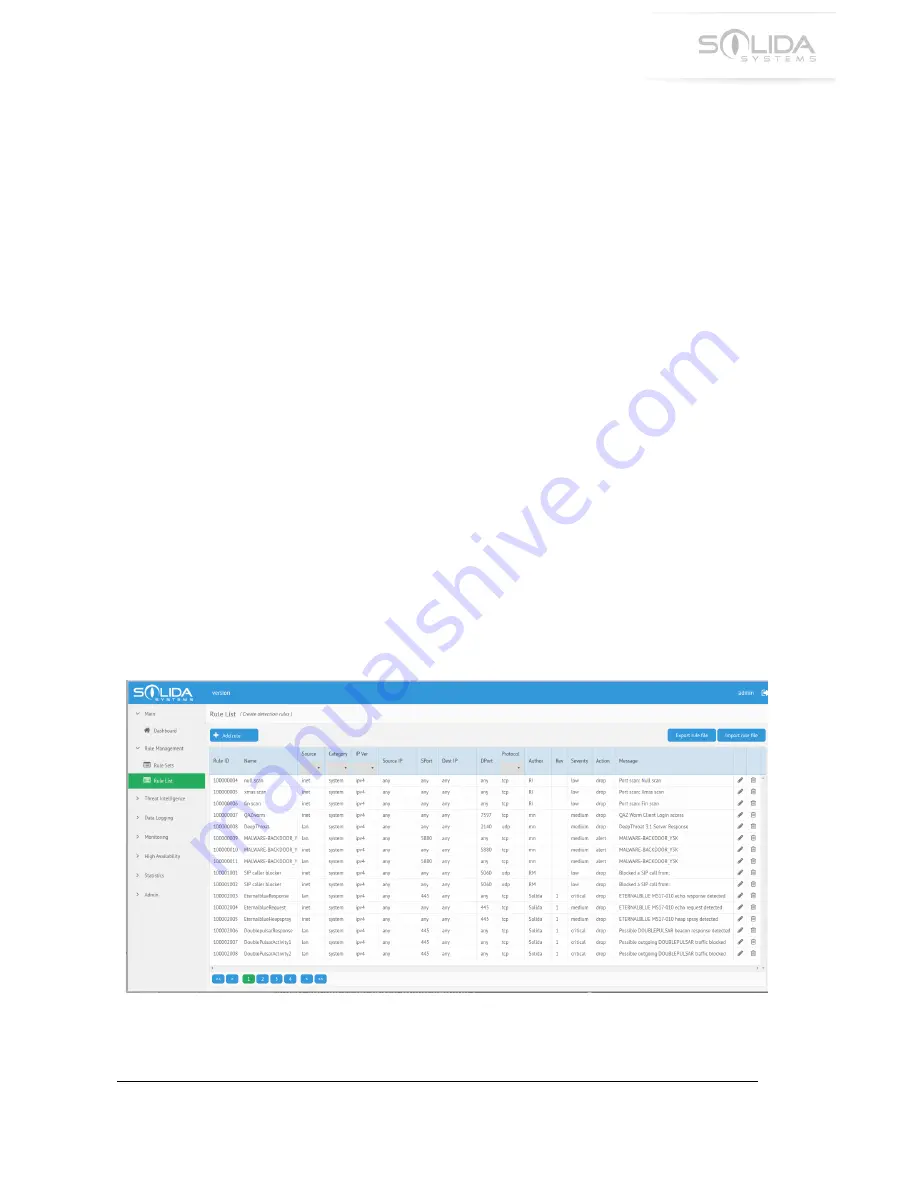
8.2 Rule List
Detection rules can be created and edited trough the configuration application. Start the
application and navigate to “Rule List”. This will show a list over all available rules in the
appliance.
Figure 8.1 Rule list in the configuration utility.








































