38
©
SOLIDA SYSTEMS INTERNATIONAL 2017
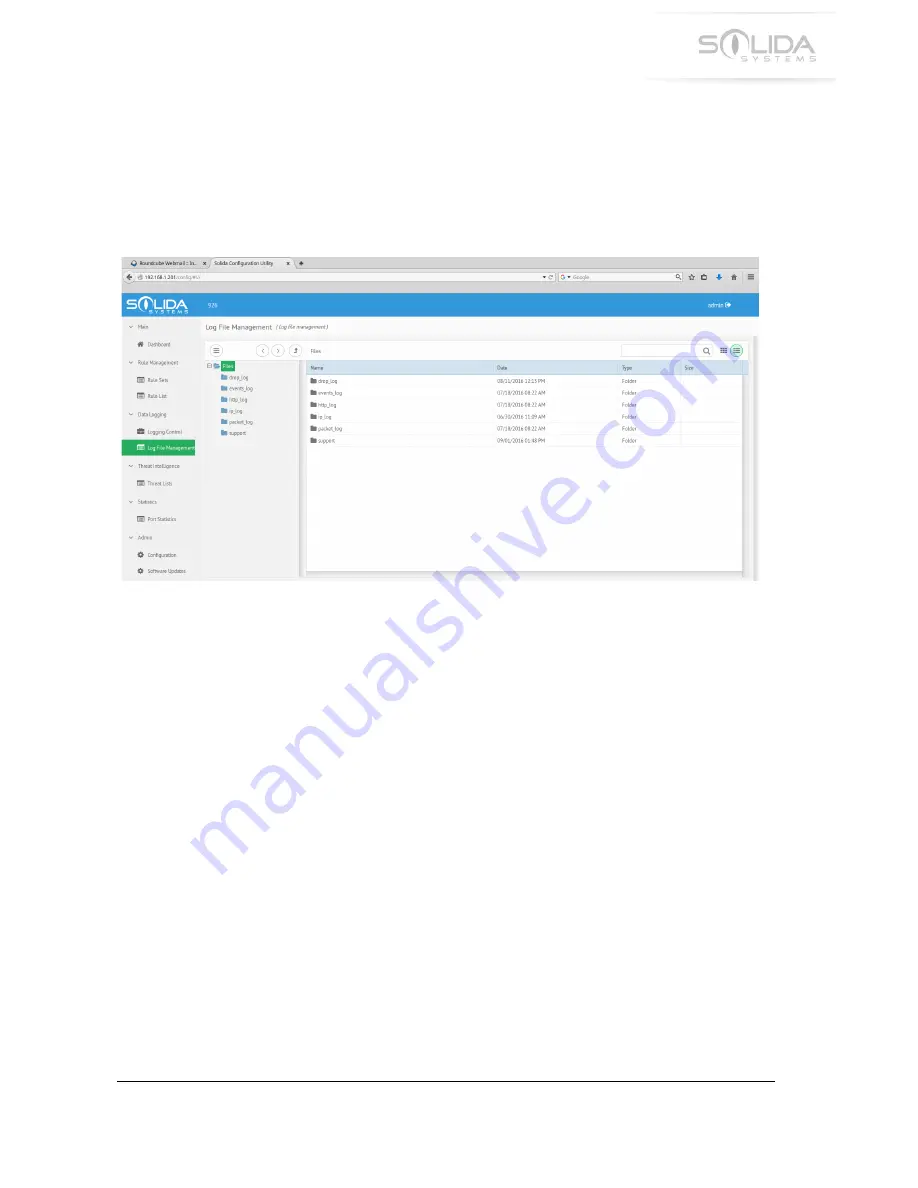
15.6 Downloading Log Files
Log files can be downloaded using either the configuration application or the monitoring
application. To download a log file, navigate to the “Log File Management” menu option. This will
open up a file management interface as shown in the picture below:
Figure 15.4 Log file management window.
Each category of log file will be stored in its own dedicated directory. Open the directory
containing the desired log file to download. Double click on the log file. A popup window will ask
for a final confirmation before the file download starts.
15.7 Deleting Log Files
The log files can easily be deleted if needed. Navigate into a log file directory. To delete a file
within the directory, right-click on the file and select ‘Delete’. The file will be permanently deleted
from the appliance.
It is also possible to rename a log file. Right-click on the file to rename it.
Even though possible, never delete a log file directory.
Please note that some log files become very large. The appliance has limited space for log files,
therefore always download important log files and save them outside the appliance. The appliance
performs log rotation, which means older log files will be deleted if needed by the appliance.












































