76 Populating the topology database
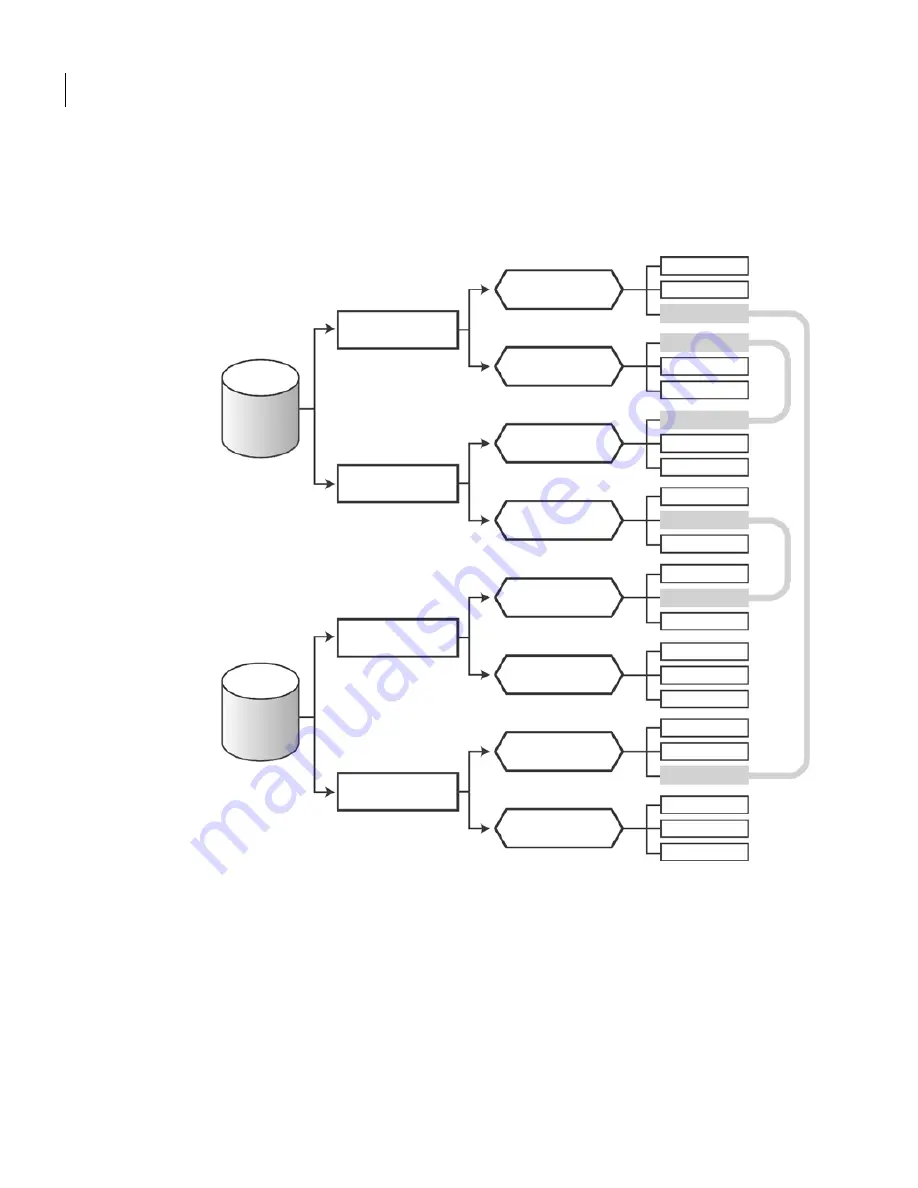
About the network topology
interfaces. This example might help you when taking inventory of your own
network topology:
Figure 4-1
Sample Network Topology Map
Gathering information
After you have taken an inventory of your existing network, you can provide
this information to the Symantec Network Security database by populating the
topology tree. To prepare for this, we recommend that you gather information
specific to each element of your topology.
This section describes the information and conventions common to most
devices and network elements that you might need to provide. Each individual
procedure includes device-specific information.
Location 1
Location 2
Segment A
Segment B
Segment C
Segment D
Device
Device
Device
Device
Device
Device
Device
Device
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Interface
Summary of Contents for 10521146 - Network Security 7120
Page 1: ...Symantec Network Security Administration Guide...
Page 12: ...12 Contents Index...
Page 14: ...14...
Page 70: ...70...
Page 110: ...110 Populating the topology database Adding nodes and objects...
Page 158: ...158 Responding Managing flow alert rules...
Page 188: ...188...
Page 242: ...242 Reporting Playing recorded traffic...
Page 268: ...268 Managing log files Exporting data...
Page 316: ...316 Advanced configuration Configuring advanced parameters...
Page 318: ...318...
Page 338: ...338 SQL reference Using MySQL tables...
Page 366: ...366 Glossary...
Page 392: ...392 Index...





































