2016 Symantec Corporation This document may be freely reproduced & distributed whole & intact including this copyright
notice.
33
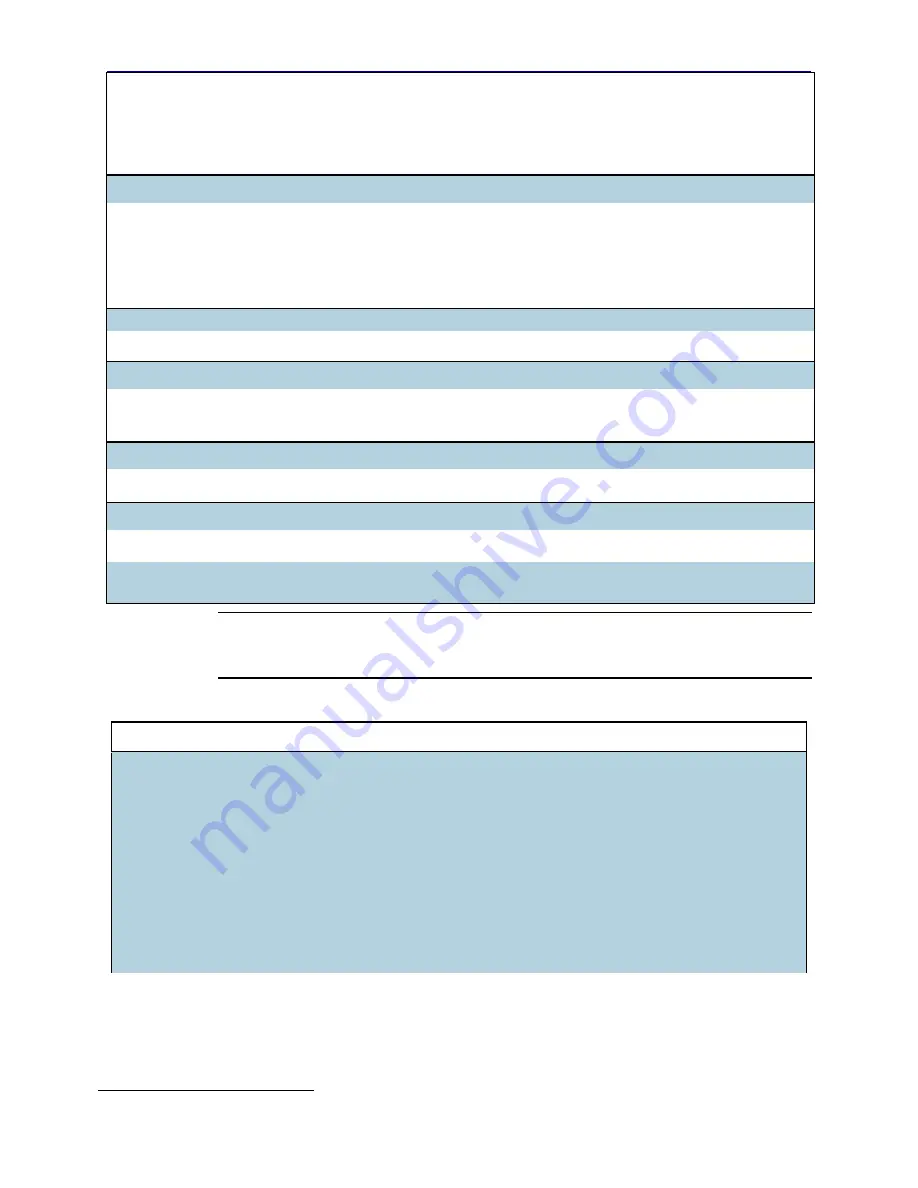
Algorithm
SSL Visibility Appliance
Crypto Library Certificate
Numbers
NFP 3240-A2
Certificate
Number
RSA (186-4) hardware signature generation 2048 bit Not Implemented
1238
ECDSA (186-4) key generation, signature
generation and verification (NIST B curves (B-233,
B-283, B-409, B-571), K curves (K-233, K-283, K-
409, K-571), and P curves (P-224, P-256, P-384, P-
521)
584, 711, and 931
Not Implemented
Hashing Functions
SHA-1, SHA-224, SHA-256, SHA-384, SHA-512
2642, 2885, and 3378
2052
Message Authentication Code (MAC) Functions
HMAC with SHA-1
1
, SHA-224, SHA-256, SHA-
384, SHA-512
2013, 2230 and 2682
Not Implemented
Random Bit Generator
SP 800-90A CTR DRBG
669, 866, and 1233
Not Implemented
Key Derivation
SP 800-132 v2 section 5.4 PBKDF option 2a
Vendor affirmed
Not Implemented
CVL (SSH, SNMP and TLS1.0/1.1/1.2)
429, 562, and 919
Not Implemented
Note:
TLS, SSH and SNMP protocols have not been reviewed or tested by the CAVP and
CMVP. See NIST SP 800-131A for more information, as some algorithms may be classified
as deprecated, restricted, or legacy-use in the upcoming algorithm transition.
Table 2
–13a SV3800/SV3800B/SV3800B-20 Non-FIPS 140-2 Approved but Allowed Security Functions
Algorithm
Details
RSA
Management TLS sessions
Only 2048 and 3072-bit RSA key sizes are used for TLS
session negotiation.
SSL/TLS Interception
RSA key sizes between 2048 and 15360-bits may be used
for session negotiation during SSL/TLS interception,
resigning server certificates during SSL/TLS interception,
making policy decisions for SSL/TLS interception, and
SSL/TLS decryption and inspection.
Key wrapping; key establishment methodologies provide
between 112 and 256 bits of encryption strength.
1
HMAC-SHA-1 uses keys of at least 112-bits of security strength.


































