Performing Advanced Configuration
SYSTIMAX® AirSPEED™ AP542
User Guide
94
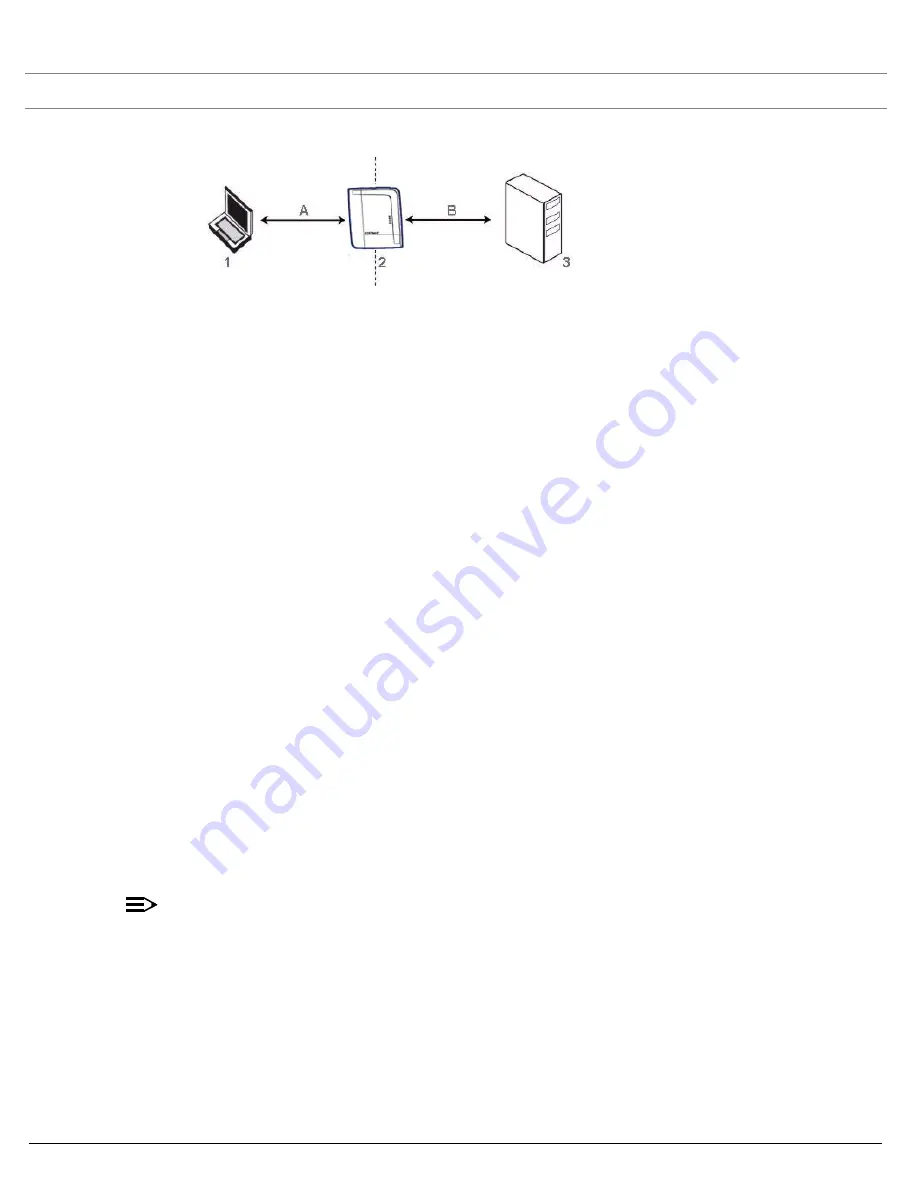
Figure 4-36 RADIUS Authentication Illustrated
The AP acts as a pass-through device to facilitate communications between the client PC and the RADIUS server. The
AP (2) and the client (1) exchange 802.1x messages using an EAPOL (EAP Over LAN) protocol (A). Messages sent
from the client station are encapsulated by the AP and transmitted to the RADIUS (3) server using EAP extensions (B).
Upon receiving a reply EAP packet from the RADIUS, the message is typically forwarded to the client, after translating
it back to the EAPOL format. Negotiations take place between the client and the RADIUS server. After the client has
been successfully authenticated, the client receives an Encryption Key from the AP (if the EAP type supports
automatic key distribution). The client uses this key to encrypt data after it has been authenticated.
For 802.11a and 802.11b/g clients that communicate with an AP, each client receives its own unique encryption key;
this is known as Per User Per Session Encryption Keys.
Wi-Fi Protected Access (WPA/WPA2)
Wi-Fi Protected Access (WPA) is a security standard designed by the Wi-Fi Alliance in conjunction with the Institute of
Electrical and Electronics Engineers (IEEE). The AP supports WPA2, defined in the IEEE 802.11i security standard.
WPA is a replacement for Wired Equivalent Privacy (WEP), the encryption technique specified by the original 802.11
standard. WEP has several vulnerabilities that have been widely publicized. WPA addresses these weaknesses and
provides a stronger security system to protect wireless networks.
WPA provides the following new security measures not available with WEP:
•
Improved packet encryption using the Temporal Key Integrity Protocol (TKIP) and the Michael Message Integrity
Check (MIC).
•
Per-user, per-session dynamic encryption keys:
–
Each client uses a different key to encrypt and decrypt unicast packets exchanged with the AP
–
A client's key is different for every session; it changes each time the client associates with an AP
–
The AP uses a single global key to encrypt broadcast packets that are sent to all clients simultaneously
–
Encryption keys change periodically based on the
Re-keying Interval
parameter
–
WPA uses 128-bit encryption keys
•
Dynamic Key distribution
–
The AP generates and maintains the keys for its clients
–
The AP securely delivers the appropriate keys to its clients
•
Client/server mutual authentication
–
802.1x
–
Pre-shared key (for networks that do not have an 802.1x solution implemented)
NOTE
For more information on WPA, see the Wi-Fi Alliance Web site at
http://www.wi-fi.org
.
The AP supports the following WPA authentication modes:
•
WPA:
The AP uses 802.1x to authenticate clients. You should only use an EAP that supports mutual authentication
and session key generation, such as EAP-TLS, EAP-TTLS, and PEAP. See
802.1x Authentication
for details.
•
WPA-PSK (Pre-Shared Key):
For networks that do not have 802.1x implemented, you can configure the AP to
authenticate clients based on a Pre-Shared Key. This is a shared secret that is manually configured on the AP and
each of its clients. The Pre-Shared Key must be 256 bits long, which is either 64 hexadecimal digits or 32
alphanumeric characters. The AP also supports a
PSK Pass Phrase
option to facilitate the creation of the
Pre-Shared Key (so a user can enter an easy-to-remember phrase rather than a string of characters).
















































