Midian Encryption Programming and Service Manual
System Operation
13
June 2006
© Tait Electronics Limited
1
System Operation
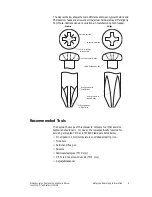
Encrypted radios provide increased privacy for conversations by jumbling
speech so that only radios with the right hardware and settings can
reconstruct it. The diagram below shows a typical radio system comprising
portable radios, mobile radios, base stations or repeaters.
Whether or not a radio transmission is encrypted is the user’s choice. When
the encryption mode is selected, the radio sends and receives encrypted calls
to and from other radios with compatible encryption module and settings.
However, even when encryption is not selected, an encryption-enabled
radio will always decode encrypted communication from any radio with
compatible modules and settings.
Note
When modules or settings are incompatible, communication is
reduced to unintelligible noise.
355
355
355
355
355
355
355
355
encrypted radios with
correct code key
=
clear
speech
radios with no
encryption module
=
unintelligible
noise
encrypted radios with
correct code key
=
clear
speech
scanner
=
unintelligible
noise
encrypted radios with
incorrect code key
radio network
=
unintelligible
noise
TB8100
10 10 1