47
Burst time
Maximum burst time is a feature based on the PRISM Nitro; a new WLAN software solution that more than triples
802.11g throughput in a mixed-mode environment and offers up to 50 percent greater throughput performance in
802.11g-only networks. PRISM Nitro is fully IEEE 802.11 compliant and uses prioritization algorithms and enhanced
protection mechanisms to significantly increase wireless networking performance.The recommended value for the
maximum burst time for 11b or the mixed 11b/g environment is 650. The 11g only mode uses the value 1400.
Beacon Period
In wireless networking, a beacon is a packet sent by a connected device to inform other devices of its presence and
readiness. When a wirelessly networked device sends a beacon, it includes with it a beacon interval which specifies
the period of time before it will send the beacon again. The interval tells receiving devices on the network how long
they can wait in low-power mode before waking up to handle the beacon. Network managers can adjust the beacon
interval, usually measured in milliseconds (ms) or its equivalent, kilo microseconds (K
μ
sec).
DTIM interval
A Delivery Traffic Indication Message (DTIM) is a signal sent as part of a beacon by an access point to a client device
in sleep mode, alerting the device to a packet awaiting delivery. A DTIM interval, also known as a Data Beacon Rate, is
the frequency at which an access point's beacon will include a DTIM. This frequency is usually measured in
milliseconds (ms) or its equivalent, kilo microseconds (K
μ
sec).
802.11d
802.11d is a wireless network communications specification for use in countries where systems using other standards
in the 802.11 family are not allowed to operate. The 802.11d specification is well suited for systems that want to
provide global roaming.
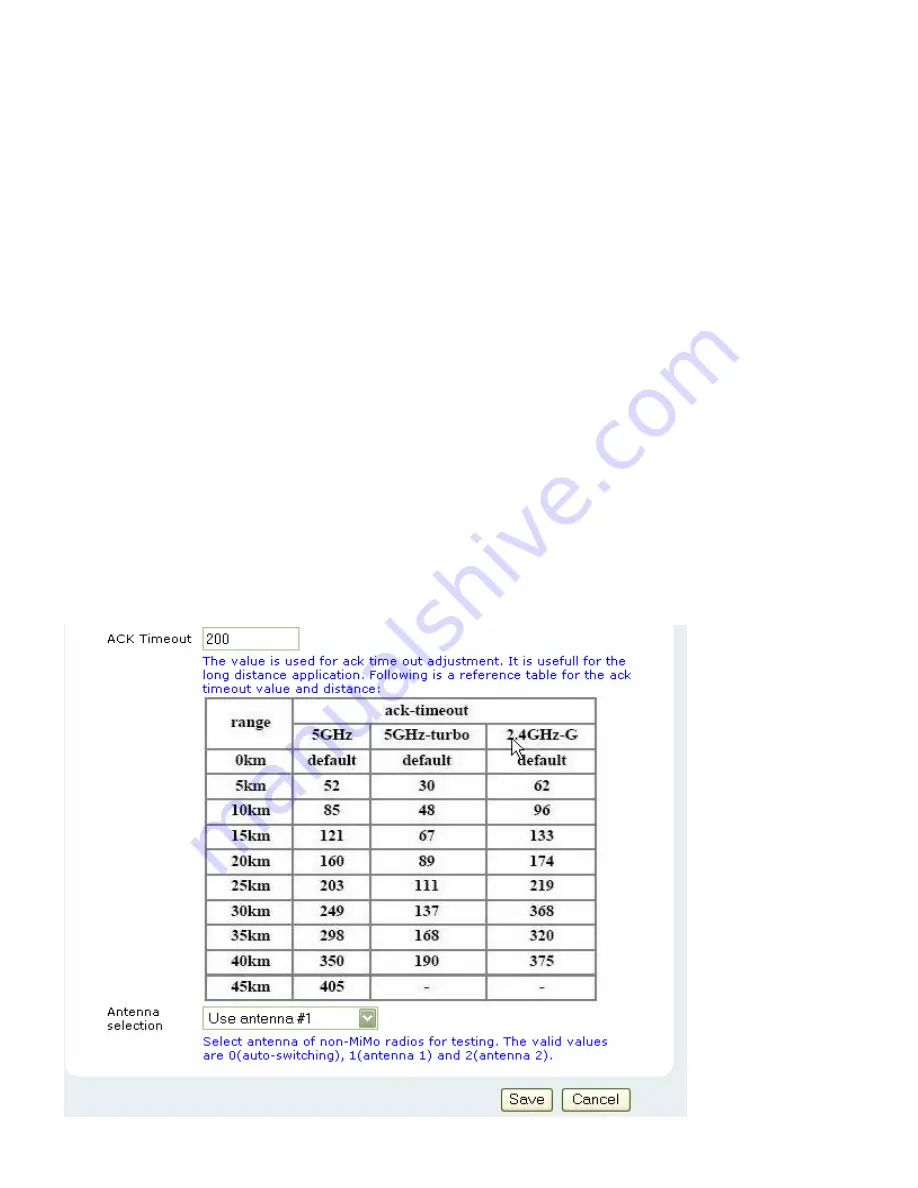
ACK Timeout
Summary of Contents for TT 900
Page 1: ...1 TT 900 User Manual 802 11b g 200mW ...
Page 11: ...11 5 Click OK to finish configuration ...
Page 14: ...14 Wireless ...
Page 18: ...18 Security ...
Page 26: ...26 Advanced ...
Page 31: ...31 Wireless ...
Page 36: ...36 Security ...
Page 42: ...42 Admin ...











































