131
9.12.2
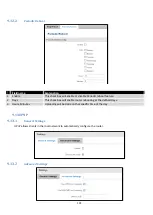
Periodic Reboot
Field name
Explanation
1. Enable
This check box will enable or disable Periodic reboot feature.
2. Days
This check box will enable router rebooting at the defined days.
3. Hours, Minutes
Uploading will be done on that specific time of the day
9.13
UPNP
9.13.1
General Settings
UPnP allows clients in the local network to automatically configure the router.
9.13.2
Advanced Settings