61
7.3.2
DHCP Server
The DHCP server is the router side service that can automatically configure the TCP/IP settings of any device that
requests such a service. If you connect a device that has been configured to obtain IP address automatically the DHCP
server will lease an IP address and the device will be able to fully communicate with the router.
7.3.2.1
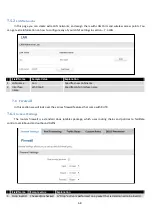
General Setup
Field Name
Sample value
Explanation
1. DHCP
Enable / Disable/
DHCP Relay
Manage DHCP server
2. Start
100
The starting address of the range that the DHCP server can use to give out to
devices. E.g.: if your LAN IP is 192.168.2.1 and your subnet mask is 255.255.255.0
that means that in your network a valid IP address has to be in the range of
[192.168.2.1 – 192.168.2.254](192.168.2.0 and 192.168.2.255 are special
unavailable addresses). If the Start value is set to 100 then the DHCP server will
only be able to lease out addresses starting from 192.168.2.100
3. Limit
150
How many addresses the DHCP server gets to lease out. Continuing on the above
example: if the start address is 192.168.2.100 then the end address will be
192.168.2.254 (100 + 155 – 1 = 254).
4. Lease time
12
How long can a leased IP be considered valid. An IP address after the specified
amount of time will expire and the device that leased it out will have to request
for a new one. Select Hour or Minute (minimum 2min).