User Guide
23
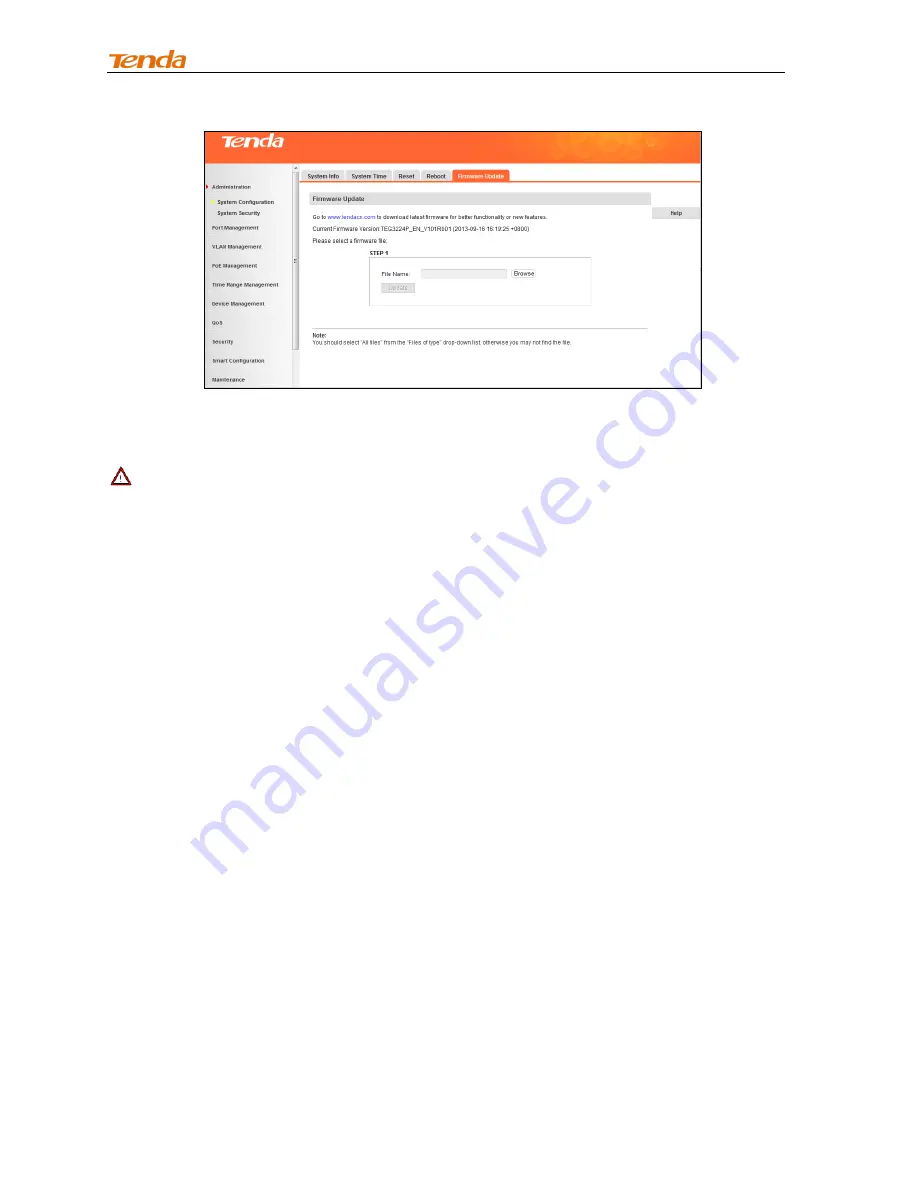
This section displays current firmware version. To update the switch's firmware, click
Browse
to locate
and select the latest firmware and click
Update
. The process takes 1-2 minutes to finish.
Note
-------------------------------------------------------------------------------------------------------------------------------
1. Do not disconnect power connection while upgrade is in process.
2. If power supply is disconnected, please upgrade it again; if unable to enter the management interface,
contact maintenance personnel.
-------------------------------------------------------------------------------------------------------------------------------------------
4.1.2 System Security
SSL Setup
Secure Sockets Layer (SSL) is a cryptographic protocol that is designed to provide communication
security over the Internet. It is widely applied in E-commerce and Internet banking areas.
SSL Security
Privacy: Adopting asymmetrical encryption technology and RSA (Rivest Shamir and Adleman), SSL uses
key pair to encrypt information.
Authentication: Authenticate the users and the servers based on the certificates to ensure the data are
transmitted to the correct users and servers. SSL server and clients obtain CA certificates via PKI (Public
Key Infrastructure).
Integrality: Maintain the integrality of the data based on Message Authentication Code (MAC) to prevent
data being altered in the transmission. A MAC algorithm, sometimes called a keyed (cryptographic) hash
function, accepts as input a secret key and an arbitrary-length message to be authenticated, and outputs
a MAC (sometimes known as a tag). The MAC value protects both a message's data integrity as well as
its authenticity, by allowing verifiers (who also possess the secret key) to detect any changes to the
message content.
SSL Protocol Structure
SSL protocol can be divided into 2 layers: The bottom layer is SSL record protocol; the top layer includes
SSL handshake protocol, SSL change cipher spec protocol and SSL alert protocol.