Options and Features Use
101
SWRU455A – February 2017 – Revised March 2017
Copyright © 2017, Texas Instruments Incorporated
Secure Socket
In server mode; if there is no DH file, the DH cipher suites are not available, even if a secured mask is
used to peek certain cipher suites with DH. If an ECDSA signature is used in the server certificate, the
RSA ciphers are not available, and vice versa.
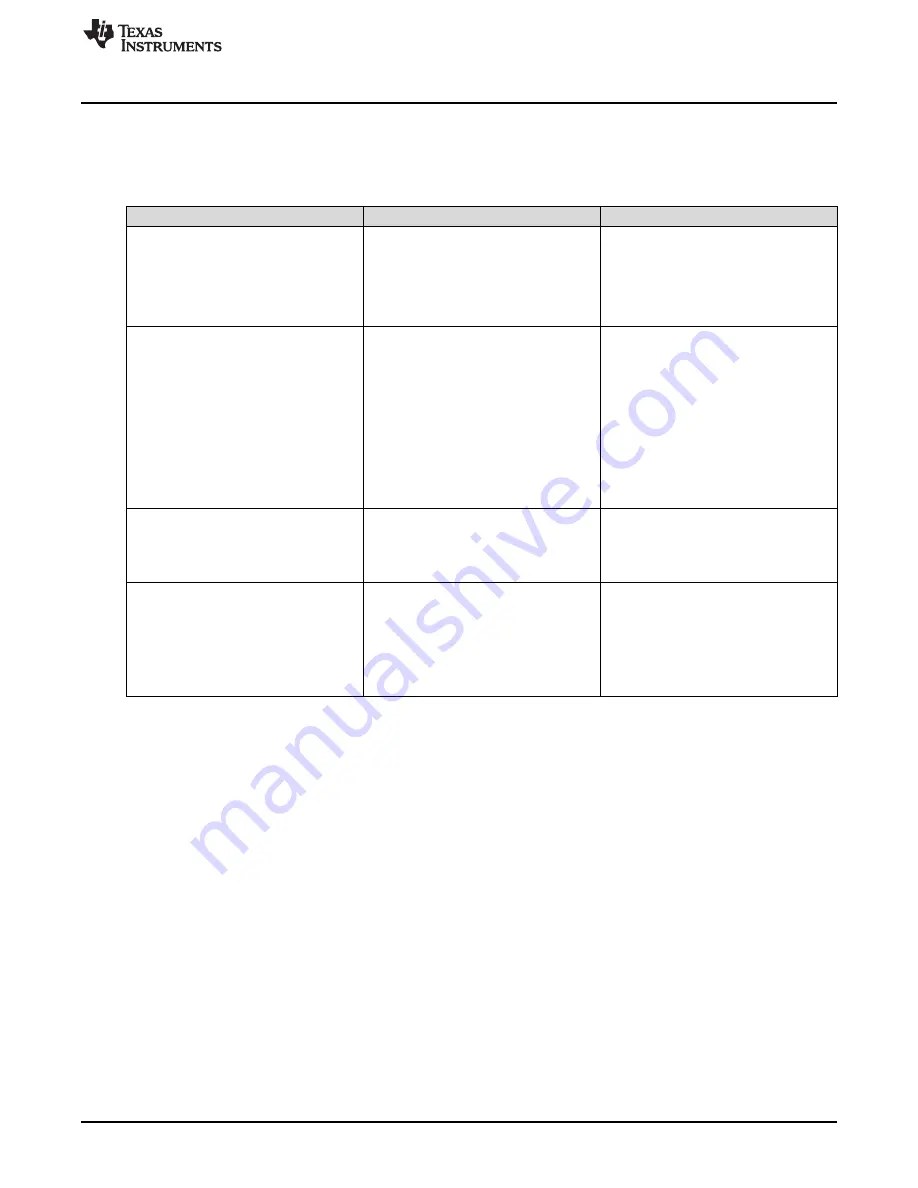
Table 7-2. Related Files
File
Client
Server
Root CA file
Format: PEM/DER.
The self-signed certificate that signed the
other peer chain
Validates the remote peer (the remote
server)
If file does not exist, connection success
with error
SL_ERROR_BSD_ESECSNOVERIFY
Enables client verification when
programmed (not mandatory).
If programmed and peer did not send its
certificate, a socket asynchronous event is
raised with error
SL_ERROR_BSD_ESEC_NO_PEER_CE
RT.
Cert
Format: PEM/DER.
A certificate issued to this peer side.
Client Cert or certificate chain if server
requires client authentication. Chain can
only be programmed in a PEM format,
where the client certificate is the first,
followed by all the intermediate CAs.
If file does not exist, and the server
requires client authentication, the server
returns ALERT of peer verify error in the
sl_Connect command.
The user must program private key with
this file, or else connection fails with
SL_ERROR_BSD_ESECBADPRIVATEFI
LE.
Server certificate or certificate chain.
Chain could only be programmed in PEM
format. The server cert should be the first
in the list.
The file must be configured. If not
configured, error
SL_ERROR_BSD_ESECBADCERTFILE
occurs.
Private Key
Format: PEM/DER.
RSA or ECDSA key.
Client private key if server requires client
auth.
The user must program cert with this file,
or else connection fails with
SL_ERROR_BSD_ESECBADCERTFILE.
The private key of the server.
Must be configured. If not configured,
error
SL_ERROR_BSD_ESECBADPRIVATEFI
LE is raised.
DH (server) or PEER Cert (client)
Format: PEM/DER.
Other side certificate or DH parameters.
Configuring this file enables the domain
verification by full server cert comparison.
This file is the server expected cert. This
is being compared to the server certificate
that was received from the server during
the handshake phase, to validate that this
is truly the domain to connect to (stronger
than the domain name verification).
DH file –Diffie Hellman parameters file.
Contains parameters for generating DH
key when using DHE cipher suites in
server mode.
Enables the DH ciphers.
Binding a file to a socket is done using sl_SetSockOpt, before the sl_Connect or sl_Listen commands.
•
SL_SO_SECURE_FILES_PRIVATE_KEY_FILE_NAME
•
SL_SO_SECURE_FILES_CERTIFICATE_FILE_NAME
•
SL_SO_SECURE_FILES_CA_FILE_NAME
•
SL_SO_SECURE_FILES_PEER_CERT_OR_DH_KEY_FILE_NAME
Example:
_i16 status;
status =
sl_SetSockOpt(sd,SL_SOL_SOCKET,SL_SO_SECURE_FILES_CA_FILE_NAME,"ca.der",strlen("ca.der"));
7.5.4 Disable the Use of the Trusted Root-Certificate Catalog
The user can disable the use of the trusted root-certificate catalog if a personal unknown root CA is used.
This is done by using this sl_SetSockOpt, before the sl_Connect or sl_Listen commands.
Example:
_u32 dummyVal;
_i16 status;
status = sl_SetSockOpt(SockID,SL_SOL_SOCKET, SL_SO_SECURE_DISABLE_CERTIFICATE_STORE,