Application Note: Security, Alarm System
17 |
E N
8
Wiegand Keypad & RFID Card Reader. Wiring & Programming.
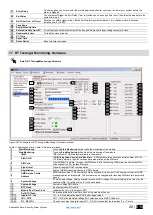
Sera2> System Options> Digital I/O Settings
Sera2> Users/ Access Control
O
U
T1
C
O
M
BU
S
O
U
T4
I/O
1
IN
4
IN
3
IN
2
D
3
O
U
T2
+3
.3
V
O
U
T3
D
1
D
2
VD
+
C
O
M
IN
1
I/O
2
1
2
3
4
5
6
7
8
9
esc
0
ENT
-
+
-
+
Bell
Buzzer
co
m
12
V
D
1
D
0
Led
Gtalarm 2
Figure 25Wiegand keypad connection
Wiegand bus specifications:
26bit Wiegand (Default);
8bit key press code
Steps to configure Wiegand keypad:
1.
Connect Wiegand keypad as shown in the Fig
2.
Install SERA2 software.
3.
Connect the module to the computer via mini USB cable.
4.
„Go to System options“> Digital I/O Settings
5.
Set Digital I/O D2 to Wiegand interface Data0
6.
Set Digital I/O D3 to Wiegand interface Data1
7.
Write configuration
Figure 26 How to find "System Options > Digital I/O Settings window
There is 3 different ways, to enter iButton, RFID keycard codes:
A) Manually in Sera2 software.
(The picture below)
In that case, you have to:
Install SERA2 software
1.
Go to “Users& Remote Control” table.
2.
Enter iButton
or RFID Keycard
codes for users.
3.
Select iButton
or RFID Keycard
action OUT/ARM/DISARM,
etc.
4.
Write the con
figuration into the module by pressing “Write” icon
B) Automatically in Sera2 software.
Association of iButton keys or
RFID Keycards
is carried out by activating
special programming mode -
by sending SMS or by pressing „Learn
iButtons/RFID mode“ in the SERA2 configuration program.
If you need to enter iButtons learning mode by SERA2 software, you have
to:
Install SERA2 software.
1.
Go to
the “System options> General system options” and press
“Start iButton/RFID programming mode” to start entering iButton
keys.
2.
Press “Stop iButton programming” to stop entering iButton keys.
3.
Write configuration by pressing “Write” icon.
C) by sending SMS message:
INST123456
˽063˽S
INST = Install. Configuration of the parameters.
123456= Installer‘s password
˽= Space character
063=
command
code
(iButton
keys
learning/deleting mode)
˽= Space character
S=iButton keys entering/deletion mode.
0-
Disable iButton keys learning mode,
1-
Enable iButton keys learning mode,
2-
iButton keys deleting mode,
3-
Delete these keys from memory,
which will be touched to the reader.
When you receive a message into your mobile phone in relation to activation of iButton key
programming mode, touch the key to the reader and its unique code will recorded into system
memory. Buzzer will notify you about successful recording by beeping twice. The system allows to
associate up to 800 iButton keys. Each time when touching the key, the system records its code till
all desirable keys will be recorded. If during 2 minutes not a single iButton key will not be learned,
the system will automatically exit keys learning mode. After finishing programming of the keys, you
might send SMS message.
You can disable recording of new keys into memory. In the event of failure to send this
message, ARM/DISARM of the system via iButton key will not operate. Control functions for all
newly associated keys will be assigned according to MASTER key. For example: If MASTER key
will control Out1, all newly associated keys will also control Out1.
You can delete all iButton keys from the memory. If you have the key, that you want to delete
from the memory, you have to send SMS, and touch the key to the reader. 2 minutes later, the
module will deactivate the keys deletion mode.