Application Note: Security, Alarm System
28 |
E N
19 Event Summary (Events)
Sera2> Event Summary
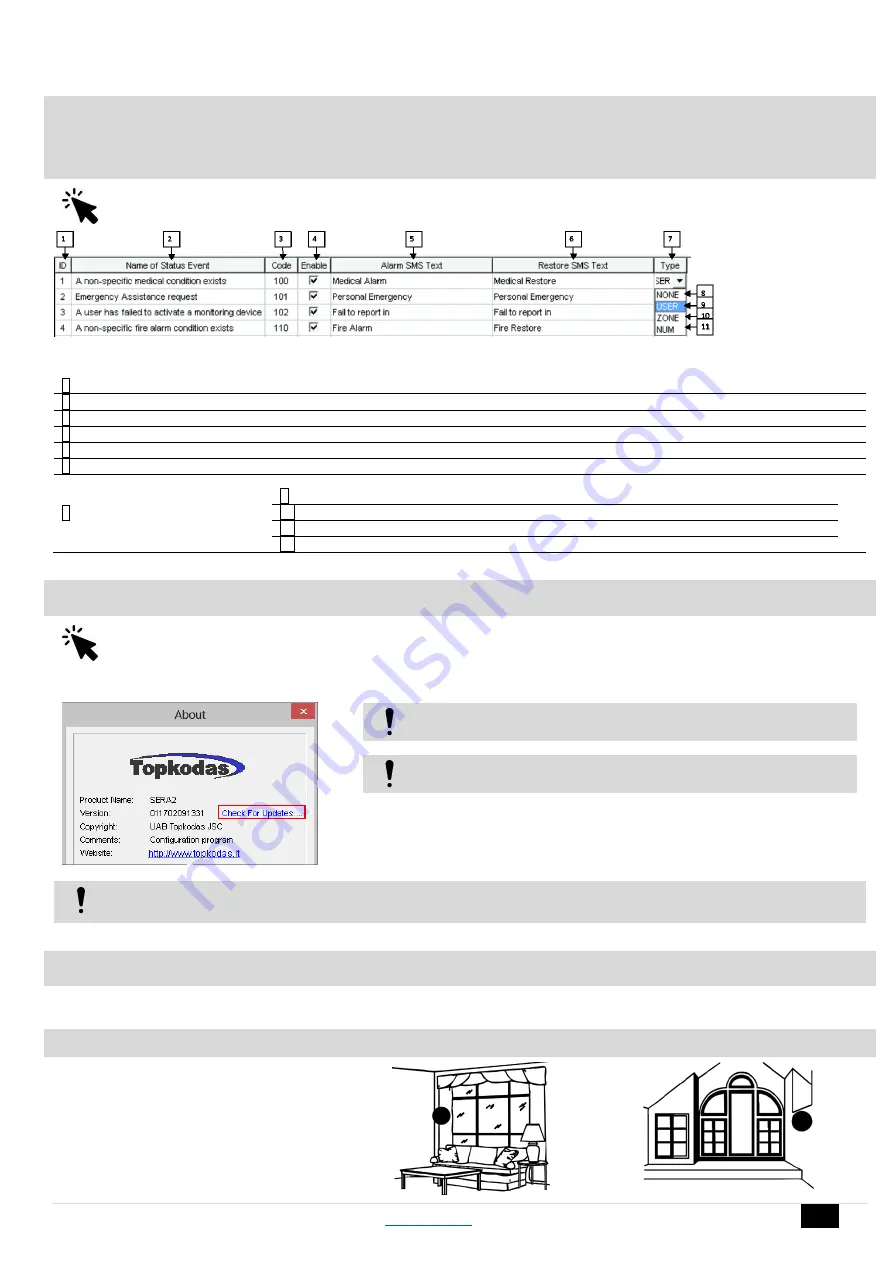
Figure 41 the example Event Summary (Events) window
Table 13 Explanation of every field in "Event Summary" window
2
ID
Report sequence number
3
Name of Status Event
Event (report) name
4
Code
Report Contact ID code.
5
Enable
The indicated report will be sent when it is checked.
6
Alarm SMS Text
Alarm text which will be visible in SMS message is entered.
7
Restore SMS Text
Restore text which will be visible in SMS message is entered.
8
Type
9
None
10
USER
Refer to USER Report Options
11
ZONE
Refer to Zone Report Options
12
NUM
Refer to Numerical Report Options
20 Software updates
Sera2> About (in the command line)
If you want to update the module manually, got to
“About” and press “Check for updates”
Figure 42 How to update the module manually
If you need to contact the seller with the questions about the configuration, you have to:
Press “Read” icon first to read the configuration from the module, the press
“File>Save us” and save the configuration.
Save the Events Log file and send these files with the question to the seller.
These steps will let better understand the problem and will reduce the time to find the solution.
If you want to receive software updates, go to Settings and mark “Check for Updates Automatically”. When new update will be available,
the program will inform you, and you have to start the update. After that you have to connect the module to the computer via mini USB
cable. You have to write this update to the module GTalarm2 by pressing “Update” in the bottom line in SERA2 software.
21 Recommendations to the installer
21.1
Glass break, shock sensors
Glass break sensors
Acoustic sensor recess mounts in a 1 in. (2.54 cm) hole.
One sensor can protect an entire room. Sensor range is 25
ft. (7.62 m) to the bottom of the g
lass in a 360˚ pattern, so
the sensor can be ceiling mounted, mounted on the opposite
wall, or on an adjoining wall.