GTalarm3 User manual V-2022-05-24
44 |
E N
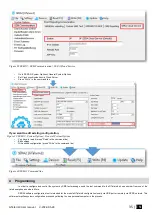
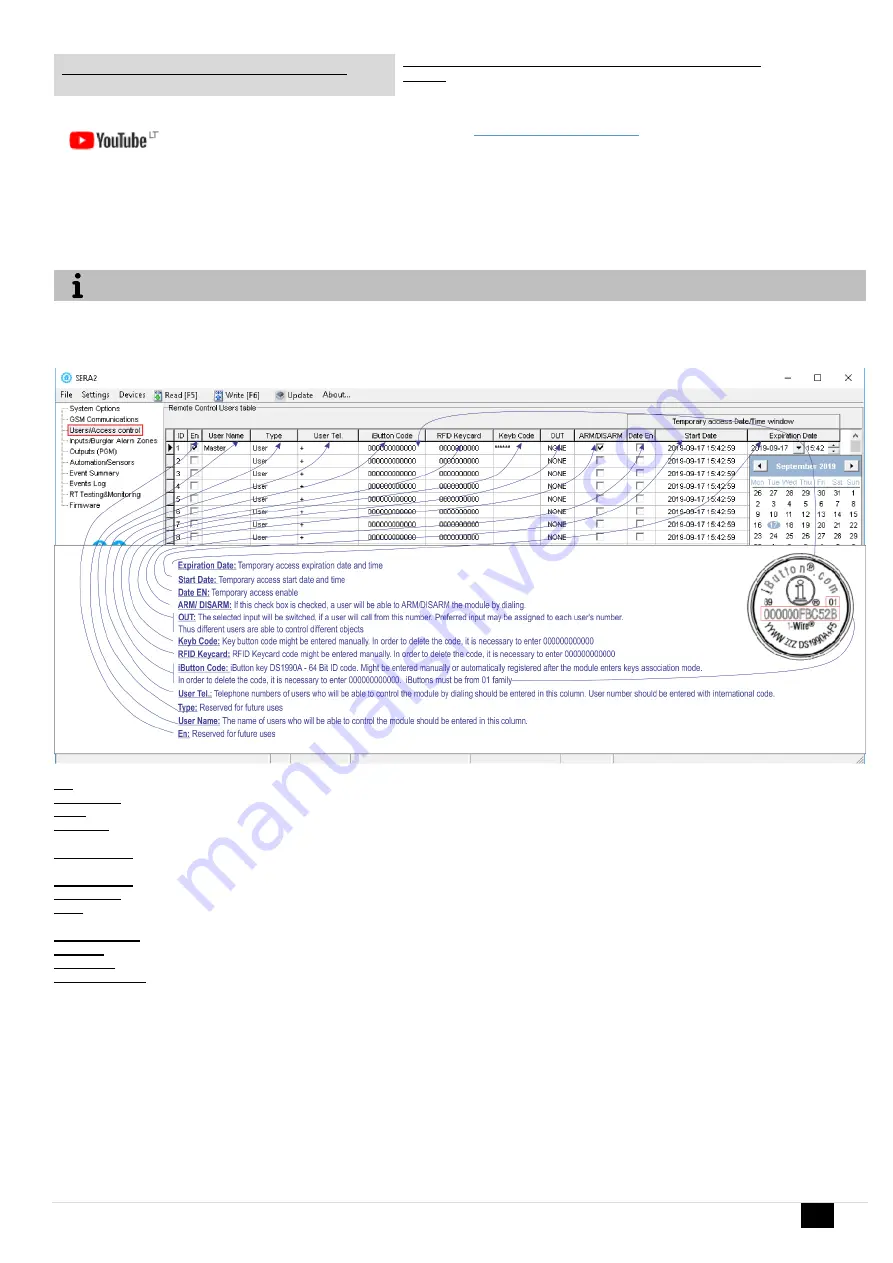
Users/ Access Control > Remote Control Users Table
The Users/ Access Control Table window let you set remote control
options.
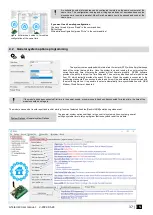
Access control: schedules, temporary access
https://youtu.be/W5FSvN-UitI
The system supports up to 800 user phone numbers for remote control purpose. When the phone number is set, the user will be able to arm/disarm
the system and control outputs by SMS text messages and free of charge phone calls as well as to configure the system by SMS text messages. By
default, the system accepts incoming calls and SMS text messages from any phone number. Once a user phone number is listed, the system ignores any
incoming calls and SMS text messages from a non-listed phone number as well as it rejects the SMS text messages containing wrong SMS password
even from a listed user phone number.
The module could be controlled only by these users, whose phone numbers entered in the memory of the module
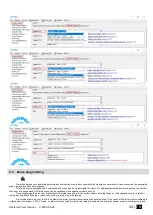
En:
Reserved for future uses
User Name:
The name of users who will be able to control the module should be entered in this column.
Type:
Reserved for future uses
User Tel.:
Telephone numbers of users who will be able to control the module by dialing should be entered in this column. User number should be
entered with international code.
iButton Code:
iButton key DS1990A - 64 Bit ID code. Might be entered manually or automatically registered after the module enters keys association
mode. In order to delete the code, it is necessary to enter 000000000000. iButtons must be from 01 family
RFID Keycard
: RFID Keycard code might be entered manually. In order to delete the code, it is necessary to enter 000000000000
Keyb Code:
Key button code might be entered manually. In order to delete the code, it is necessary to enter 000000000000
OUT:
The selected input will be switched, if a user will call from this number. Preferred input may be assigned to each user's number.
Thus different users are able to control different objects
ARM/ DISARM:
If this check box is checked, a user will be able to ARM/DISARM the module by dialing.
Date EN:
Temporary access enable
Start Date:
Temporary access start date and time
Expiration Date:
Temporary access expiration date and time
The module GTalarm3 controls access by using schedules. Inputs, outputs, readers and cards through access levels are all configured with schedules
by which they will be energized or de-energized, enabled or disabled. For example, you might assign an output to be energized from 12:00 a.m. to 6:00
a.m. every day. The 12:00 a.m. to 6:00 a.m., Monday through Sunday, time period is called a schedule. The “Access Schedules” tab enables you to
create the schedule you will use to configure your GTM module. Click “Access Schedules” tab to display the Schedules screen: