GTalarm3 User manual V-2022-05-24
28 |
E N
if output will have definition [
Automation / CTRL
] it also can be controlled by user in any ways but it will not generate 421 and 422 events,
And will not care about ARM/DISARM
Event log e.g.
1853 Event:1234:1:401:01:001 Time:2017-08-20 14:42:36 Note: , Open by User, User:001, Name:Master
1852 Event:1234:1:422:00:001 Time:2017-08-20 14:41:41 Note: , Access Gained by, User:001, Name:Master
1851 Event:1234:1:406:01:001 Time:2017-08-20 14:41:27 Note: , Cancel, User:001, Name:Master
3.5.3
Quick start outputs
1.
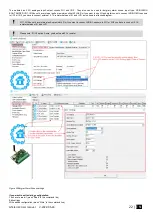
Install SERA2 software. For more information look at
SERA2 Uploading/Downloading Software
2.
Connect the module to the computer via mini USB cable.
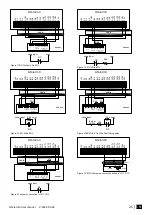
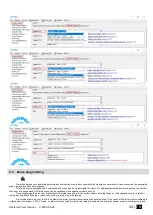
Figure 29 Outputs settings
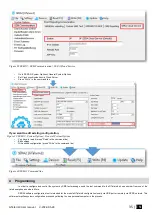
If you want to edit existing configuration
,
You have to read it (press “Read” in the command line)
Edit settings
Write edited configuration (press “Write” in the command line)
Outputs can be controlled only in Automation/ CTRL mode.
In order to control big power alternating current equipment, it is comfortable to use solid state relays.
Standard AC/DC adapter with the voltage 10V-14V and current >=1A might be used to powering the module.
3.6
Access control. Arming/Disarming methods
Arming process:
If ready
(no violated zone/tamper),
the system will arm
.
If unready
(violated zone/tamper is present), the system will not arm and
provide a list of violated zones/tampers
by SMS text message
to user phone number. In such case the user
must restore all violated zones and tampers
before arming the system. Alternatively, the
violated zones can be
bypassed, disabled or a Force
attribute enabled, and the tampers can be disabled when arming. The system initiates
the exit delay countdown intended for the user to leave the secured area.
The alarm will be caused even if a tamper is violated while the system is disarmed
Due to security reasons it is highly recommended to restore the violated zone/tamper before arming the system.
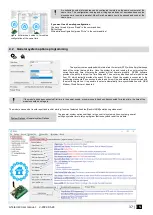
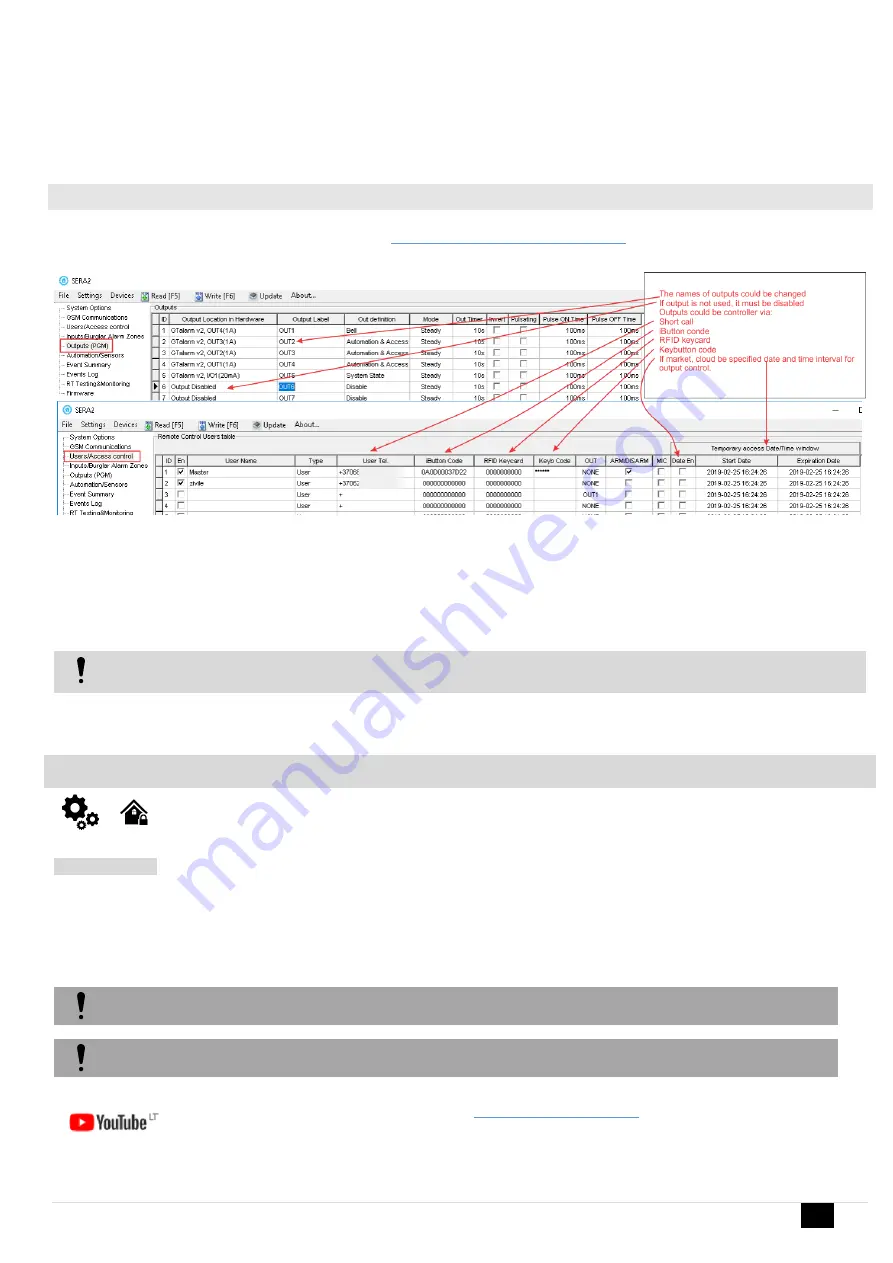
Access control: schedules, temporary access
https://youtu.be/W5FSvN-UitI
Access control methods is defined in Sera2> User/ Access control window