User Guide
388
Configuring Spanning Tree
Spanning Tree
MST Instance
The MST instance is a spanning tree running in the MST region. Multiple MST instances can
be established in one MST region and they are independent of each other. As is shown in
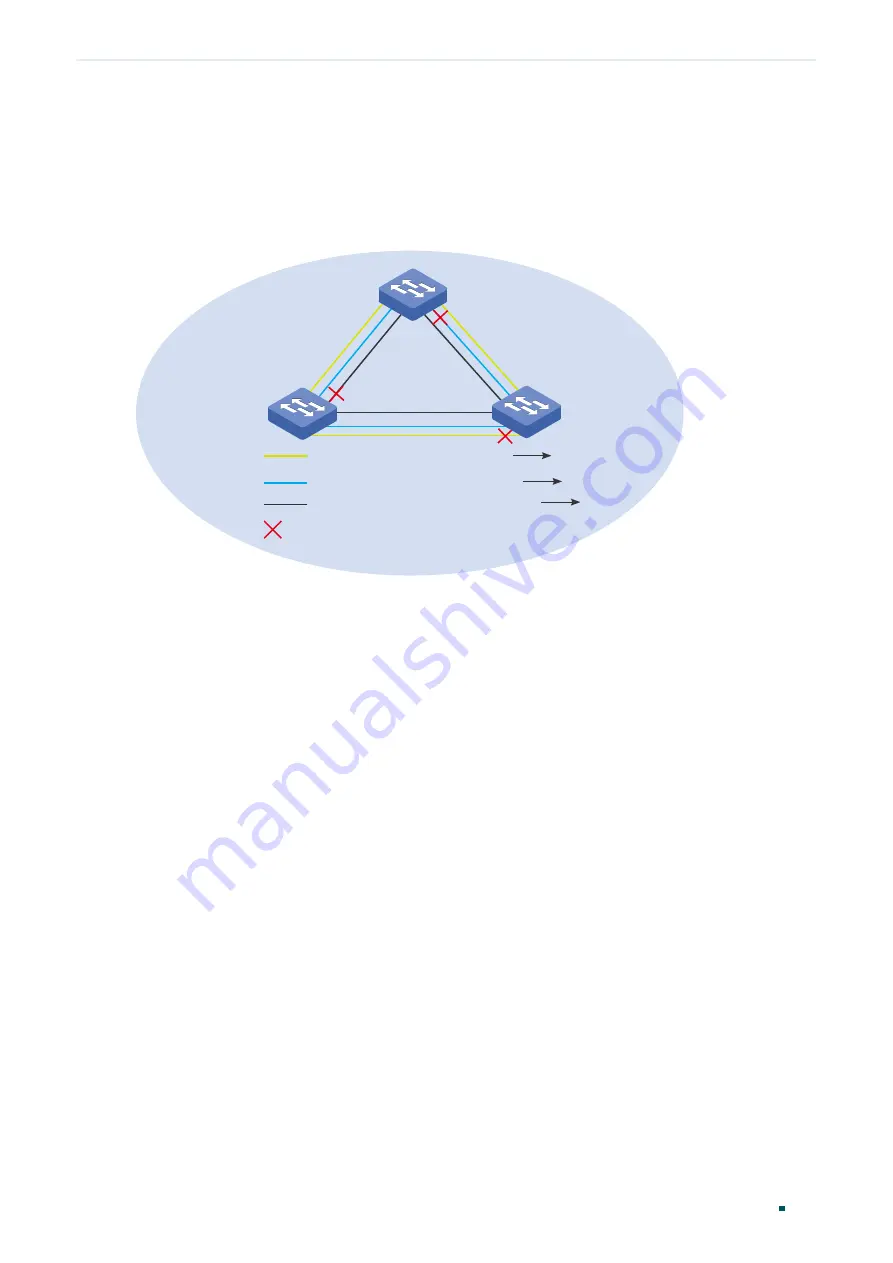
Figure 1-4, there are three instances in a region, and each instance has its own root bridge.
Figure 1-4
MST Region
A
C
Instance 1 (root bridge: A) VLAN 3 Instance 1
VLAN 4-5 Instance 2
Other VLANs IST
Instance 2 (root bridge: B)
IST (root bridge: C)
Blocked port
B
VLAN-Instance Mapping
VLAN-Instance Mapping describes the mapping relationship between VLANs and
instances. Multiple VLANs can be mapped to a same instance, but one VLAN can be
mapped to only one instance. As Figure 1-4 shows, VLAN 3 is mapped to instance 1, VLAN
4 and VLAN 5 are mapped to instance 2, the other VLANs are mapped to the IST.
IST
The Internal Spanning Tree (IST), which is a special MST instance with an instance ID 0. By
default, all the VLANs are mapped to IST.
CST
The Common Spanning Tree (CST), that is the spanning tree connecting all MST regions.
As is shown in Figure 1-3, region1-region 4 are connected by the CST.
CIST
The Common and Internal Spanning Tree (CIST), comprising IST and CST. CIST is the
spanning tree that connects all the switches in the network.
1.3 STP Security
STP Security prevents the loops caused by wrong configurations or BPDU attacks. It
contains Loop Protect, Root Protect, BPDU Protect, BPDU Filter and TC Protect functions.
Summary of Contents for JetStream T2600G-28TS
Page 264: ...Configuring VLAN VPN Configuration Examples User Guide 235 Figure 4 2 Create VLAN 100 ...
Page 265: ...User Guide 236 Configuring VLAN VPN Configuration Examples Figure 4 3 Create VLAN 200 ...
Page 268: ...Configuring VLAN VPN Configuration Examples User Guide 239 Figure 4 7 Creating VLAN 100 ...
Page 275: ...User Guide 246 Configuring VLAN VPN Configuration Examples Figure 4 11 Create VLAN 100 ...
Page 276: ...Configuring VLAN VPN Configuration Examples User Guide 247 Figure 4 12 Create VLAN 200 ...
Page 277: ...User Guide 248 Configuring VLAN VPN Configuration Examples Figure 4 13 Create VLAN 1050 ...
Page 280: ...Configuring VLAN VPN Configuration Examples User Guide 251 Figure 4 18 Creating VLAN 100 ...
Page 859: ...User Guide 830 Configuring ACL Configuration Example for ACL Figure 3 18 Configuring Rule 3 ...
Page 874: ...Configuring ACL User Guide 845 ...
Page 975: ...Part 33 Monitoring Traffic CHAPTERS 1 Traffic Monitor 2 Appendix Default Parameters ...
















































