-80-
phase 2, the
security protocols in IPsec and
he transmission data.
3.5.1.1
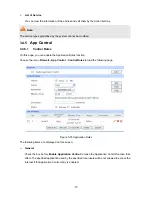
IKE Policy
On this page you can con
Choose the menu
VPN
IKE peers use the ISAKMP SA established in Phase 1 to negotiate the parameters for
create IPsec SA to secure t
figure the related parameters for IKE negotiation.
→
IKE
→
IKE Policy
to load the following page.
Figure 3-58 IKE Policy
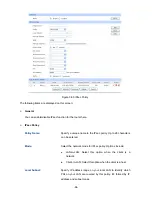
The fo
re displa
IKE Pol cy
Policy Name:
ique name to the IKE policy for identification and
The IKE policy can be applied to IPsec policy.
llowing items a
yed on this screen:
i
Specify a un
management purposes.