-86-
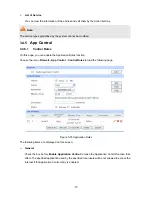
Manual Mode
IPsec Proposal:
Select the IPsec Proposal. Only one proposal can be selected
on Manual mode. You need to first create the IPsec Proposal.
.
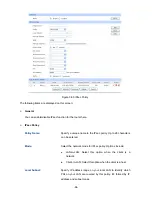
AH Authentication Key-In:
Specify the inbound AH Authentication Key manually if AH
protocol is used in the corresponding IPsec Proposal. The
inbound key here must match the outbound AH authentication
the other end of the tunnel, and vice versa.
Specify the inbound ESP Authentication Key manually if ESP
protocol is used in the corresponding IPsec Proposal. The
t match the outbound ESP authentication
ESP Encryption: Key-In:
Specify the inbound ESP Encryption Key manually if ESP
protocol is used in the corresponding IPsec Proposal. The
inbound key here must match the outbound ESP encryption key
at the other end of the tunnel, and vice versa.
Outgoing SPI:
Specify the Outgoing SPI (Security Parameter Index) manually.
The Outgoing SPI here must match the Incoming SPI value at
the other end of the tunnel, and vice versa.
AH Authentication Key-Out:
Specify the outbound AH Authentication Key manually if AH
protocol is used in the corresponding IPsec Proposal. The
outbound key here must match the inbound AH authentication
nnel, and vice versa.
outbound ESP Authentication Key manually if ESP
protocol is used in the corresponding IPsec Proposal. The
outbound key here must match the inbound ESP authentication
key at the other end of the tunnel, and vice versa.
Status:
Activate or inactivate the entry.
Incoming SPI:
Specify the Incoming SPI (Security Parameter Index) manually
The Incoming SPI here must match the Outgoing SPI value at
the other end of the tunnel, and vice versa.
key at
ESP Authentication Key-In:
inbound key here mus
key at the other end of the tunnel, and vice versa.
key at the other end of the tu
ESP Authentication Key-Out:
Specify the