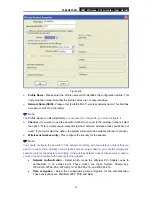
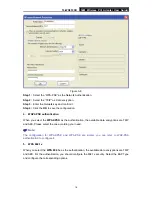
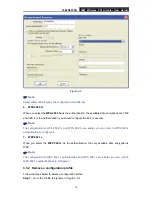
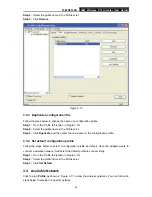
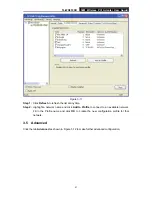
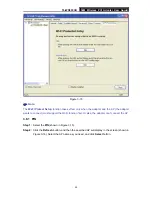
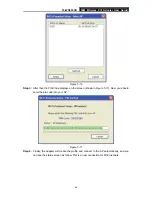
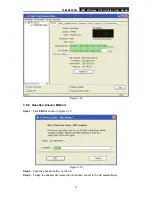
TL-WN353GD
54M Wireless PCI Adapter User Guide
29
Appendix B: Glossary
¾
802.11b -
The 802.11b standard specifies a wireless product networking at 11 Mbps using
direct-sequence spread-spectrum (DSSS) technology and operating in the unlicensed radio
spectrum at 2.4GHz, and WEP encryption for security. 802.11b networks are also referred to
as Wi-Fi networks.
¾
802.11g
-
specification for wireless networking at 54 Mbps using direct-sequence
spread-spectrum (DSSS) technology, using OFDM modulation and operating in the
unlicensed radio spectrum at 2.4GHz, and backward compatibility with IEEE 802.11b devices,
and WEP encryption for security.
¾
Ad-hoc Network -
An ad-hoc network is a group of computers, each with a Wireless PCI
Adapter, connected as an independent 802.11 wireless LAN. Ad-hoc wireless computers
operate on a peer-to-peer basis, communicating directly with each other without the use of an
access point. Ad-hoc mode is also referred to as an Independent Basic Service Set (IBSS) or
as peer-to-peer mode, and is useful at a departmental scale or SOHO operation.
¾
DSSS
(
D
irect-
S
equence
S
pread
S
pectrum)
-
DSSS generates a redundant bit pattern for all
data transmitted. This bit pattern is called a chip (or chipping code). Even if one or more bits
in the chip are damaged during transmission, statistical techniques embedded in the receiver
can recover the original data without the need of retransmission. To an unintended receiver,
DSSS appears as low power wideband noise and is rejected (ignored) by most narrowband
receivers. However, to an intended receiver (i.e. another wireless LAN endpoint), the DSSS
signal is recognized as the only valid signal, and interference is inherently rejected (ignored).
¾
FHSS
(
F
requency
H
opping
S
pread
S
pectrum)
-
FHSS continuously changes (hops) the
carrier frequency of a conventional carrier several times per second according to a
pseudo-random set of channels. Because a fixed frequency is not used, and only the
transmitter and receiver know the hop patterns, interception of FHSS is extremely difficult.
¾
Infrastructure Network -
An infrastructure network is a group of computers or other devices,
each with a Wireless PCI Adapter, connected as an 802.11 wireless LAN. In infrastructure
mode, the wireless devices communicate with each other and to a wired network by first
going through an access point. An infrastructure wireless network connected to a wired
network is referred to as a Basic Service Set (BSS). A set of two or more BSS in a single
network is referred to as an Extended Service Set (ESS). Infrastructure mode is useful at a
corporation scale, or when it is necessary to connect the wired and wireless networks.
¾
Spread Spectrum -
Spread Spectrum technology is a wideband radio frequency technique
developed by the military for use in reliable, secure, mission-critical communications systems.
It is designed to trade off bandwidth efficiency for reliability, integrity, and security. In other
words, more bandwidth is consumed than in the case of narrowband transmission, but the
trade off produces a signal that is, in effect, louder and thus easier to detect, provided that the
receiver knows the parameters of the spread-spectrum signal being broadcast. If a receiver is
not tuned to the right frequency, a spread-spectrum signal looks like background noise.
There are two main alternatives, Direct Sequence Spread Spectrum (DSSS) and Frequency