Understanding Trend Micro™ Network VirusWall™ Enforcer 2500
1
-
41
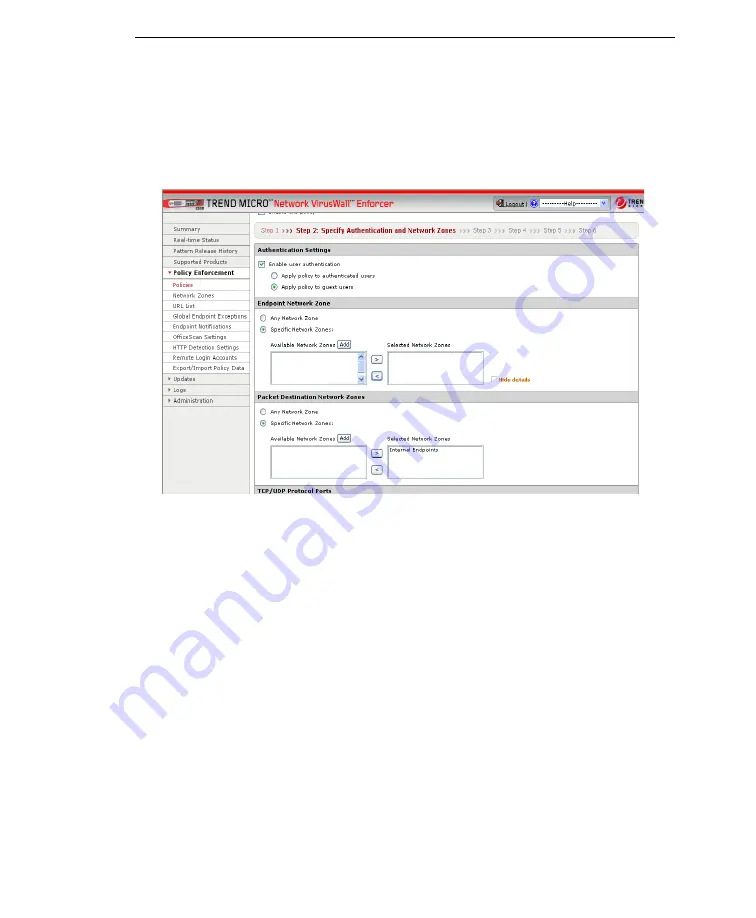
Sample Policy 2: Guest users
For the second policy, specify the required registry key if guest users try to access
endpoints belonging to the network.
F
IGURE
1-10.
Sample Policy 2: Guest users Step 2
In
Step 2
:
•
Select
Enable user authentication
and
Apply this policy to guest users
.
•
Select
Any source
.
•
Select "Internal Endpoints" as the
Destination
.
















































