Trend Micro™ Network VirusWall™ Enforcer 2500 Administrator’s Guide
1
-
42
F
IGURE
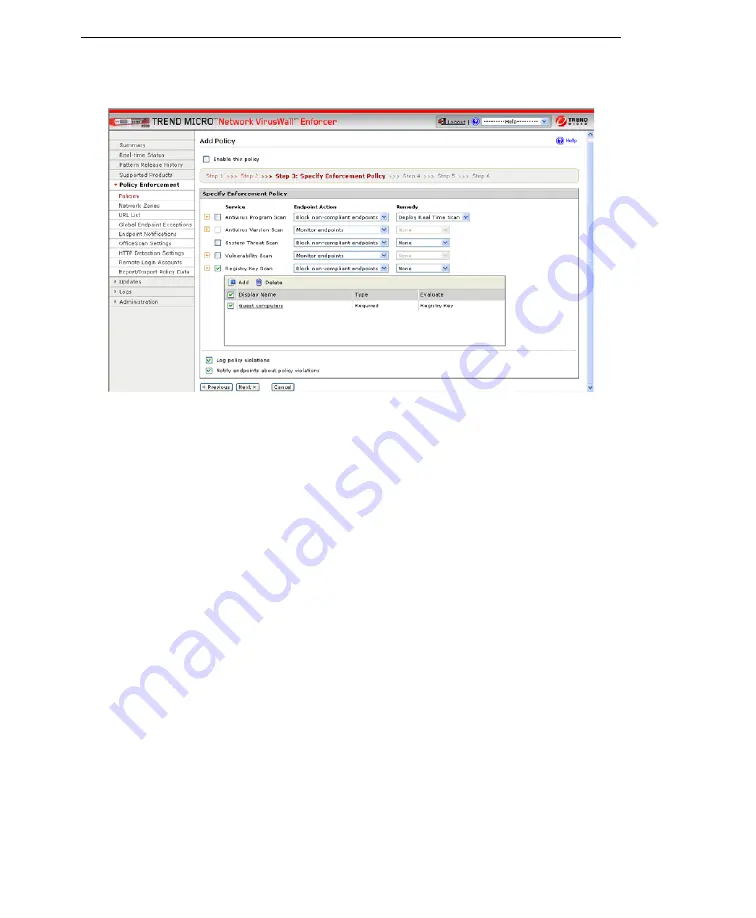
1-11.
Sample Policy 2: Guest users Step 3
In
Step3
:
•
Select
Registry Key Scan
and add the registry key as required.
•
Select to
Block non-compliant endpoints
to block endpoints that do not have
any of these applications installed.
•
Select
Log policy violation
and
Notify endpoints about policy violations
to
record and send a blocking page to the endpoint with a notification message.
















































