Trend Micro™ Network VirusWall™ Enforcer 1500i Installment and Deployment Guide
1-6
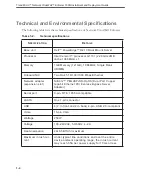
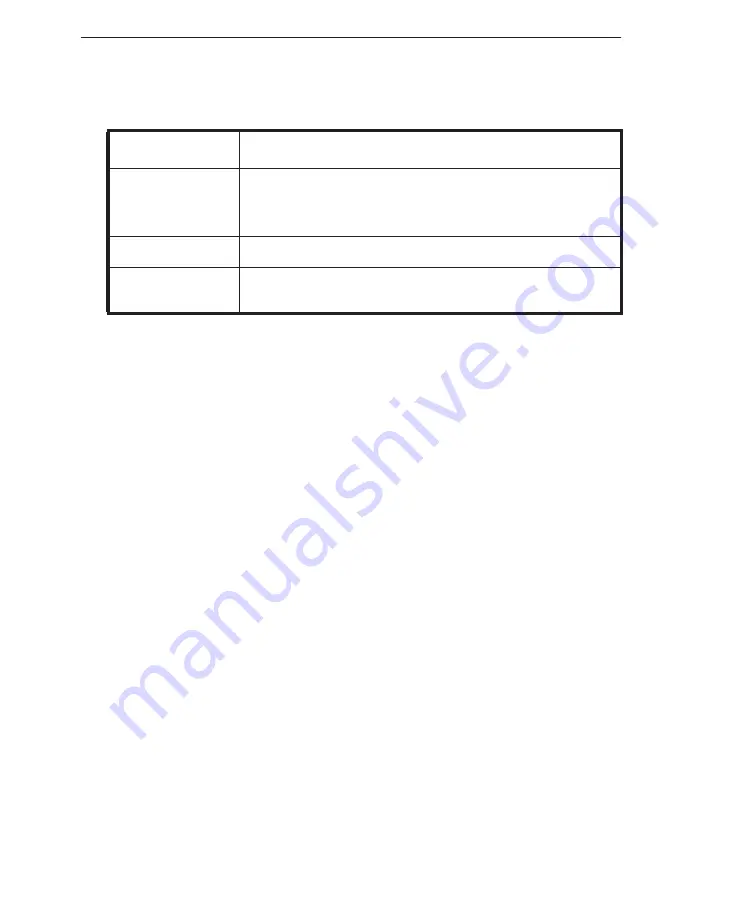
Altitude (operat-
ing)
-16 to 3048 m (-50 to 10,000 ft)
For altitudes above 2950ft, the maximum operating tem-
perature is derated 1ºF/550ft.
Altitude (storage)
-16 to 10,600 m (-50 to 35,000 ft)
Airborne contami-
nants
G2 or lower as defined by ISA-S71.04-1985
T
ABLE
1-3.
Environmental specifications (Continued)
S
PECIFICATION
D
ETAILS
Summary of Contents for viruswall enforcer 1500i
Page 1: ......
Page 7: ...Trend Micro Network VirusWall Enforcer 1500i Installment and Deployment Guide vi...
Page 13: ...Trend Micro Network VirusWall Enforcer 1500i Installment and Deployment Guide xii...
Page 30: ...Getting Started 2 11 FIGURE 2 7 Standard four port configuration Port 1 Port 3 Port 4 Port 2...
Page 59: ...Trend Micro Network VirusWall Enforcer 1500i Installment and Deployment Guide 3 20...
Page 78: ......