Trend Micro™ Network VirusWall™ Enforcer 1500i Installment and Deployment Guide
4-4
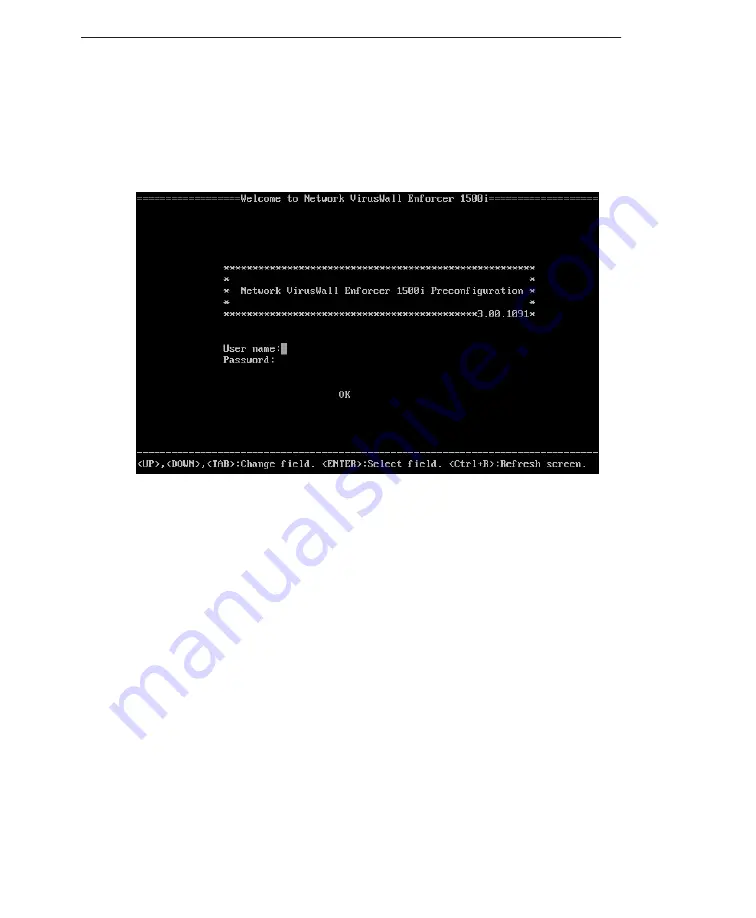
Logging on the Preconfiguration Console
A few minutes after powering on the device, the attached monitor will display the
Preconfiguration console. If this screen does not display, press CTRL+R.
F
IGURE
4-1.
The Preconfiguration console logon screen
Summary of Contents for viruswall enforcer 1500i
Page 1: ......
Page 7: ...Trend Micro Network VirusWall Enforcer 1500i Installment and Deployment Guide vi...
Page 13: ...Trend Micro Network VirusWall Enforcer 1500i Installment and Deployment Guide xii...
Page 30: ...Getting Started 2 11 FIGURE 2 7 Standard four port configuration Port 1 Port 3 Port 4 Port 2...
Page 59: ...Trend Micro Network VirusWall Enforcer 1500i Installment and Deployment Guide 3 20...
Page 78: ......
















































