247
7.1.3.2
Filter Table
Dynamic ARP inspections validates the packet by performing IP to MAC address binding
inspection stored in a trusted database (the DHCP snooping database) before forwarding the
packet. When the Switch identifies an unauthorized ARP packet, it automatically creates a MAC
address filter to block traffic from the source MAC address and source VLAN ID of the
unauthorized ARP packet. The switch also periodically deletes entries if the age-time for the
entry is expired.
If the ARP Inspection is enabled and the system detects invalid hosts, the system will create
a filtered entry in the MAC address table.
When Port link down and ARP Inspection was disabled, Switch will remove the MAC-filter
entries learned by this port.
When Port link down and ARP Inspection was enabled, Switch will remove the MAC-filter
entries learned by this port.
The maximum entry of the MAC address filter table is 256.
When MAC address filter table of ARP Inspection is full, the Switch receives unauthorized
ARP packet, and it automatically creates a SYSLOG and drop this ARP packet. The
SYSLOG event happens on the first time.
7.1.3.2.1
CLI Configurations
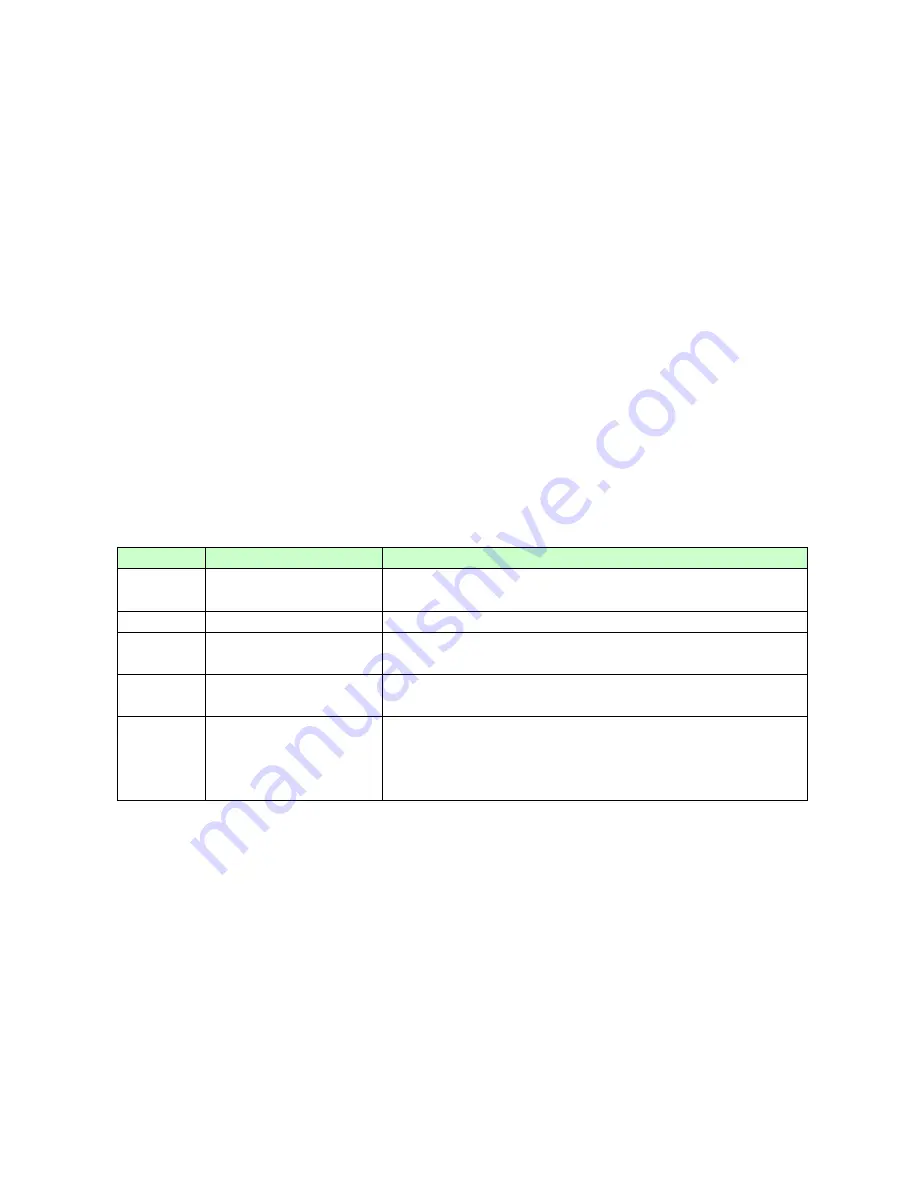
Node
Command
Description
enable
show arp-inspection
mac-filter
This command displays the current ARP Inspection
filtered MAC.
enable
configure terminal
This command changes the node to configure node.
configure arp-inspection mac-
filter age <1-10080>
This command configures the age time for the ARP
inspection MAC filter entry.
configure clear arp-inspection
mac-filter
This command clears all of entries in the filter table.
configure no arp-inspection
mac-filter mac
MACADDR vlan <1-
4094>
This command removes an entry from the ARP
inspection MAC filter table.
Summary of Contents for NGI-M08C4POE8-2
Page 1: ......
Page 197: ...197 Clear Clear the statistics of the valn ...
Page 298: ...298 9 2 2 Web Configurations ...