249
7.2
ACL
Access control list
(
ACL
) is a list of permissions attached to an object. The list specifies who or
what is allowed to access the object and what operations are allowed to be performed on the
object.
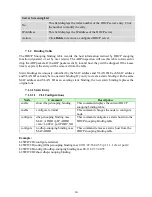
L2 ACL function allows user to configure a few rules to reject packets from the specific ingress
ports or all ports. These rules will check the packets’ source MAC address and destination MAC
address. If packets match these rules, the system will do the actions “deny”. “deny” means
rejecting these packets.
The Action Resolution engine collects the information (action and metering results) from the hit
entries: if more than one rule matches, the actions and meter/counters are taken from the policy
associated with the matched rule with highest priority.
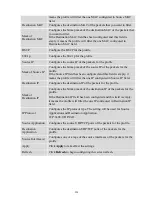
L2 ACL Support:
1. Filter a specific source MAC address.
Command:
sourcemac host MACADDR
2. Filter a specific destination MAC address.
Command:
destination mac host MACADDR
3. Filter a range of source MAC address.
Command:
sourcemac MACADDR MACADDR
The second MACADDR is a mask, for example: ffff.ffff.0000
4. Filter a range of destination MAC address.
Command:
destination mac MACADDR MACADDR
The second MACADDR is a mask, for example: ffff.ffff.0000
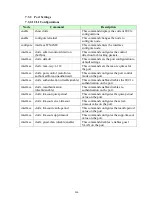
L3 ACL Support:
1. Filter a specific source IP address.
Command:
source ip host IPADDR
2. Filter a specific destination IP address.
Command:
destination iphost IPADDR
3. Filter a range of source IP address.
Command:
source ip IPADDRIPADDR
The second IPADDR is a mask, for example: 255.255.0.0
4. Filter a range of destination IP address.
Command:
destinationip IPADDRIPADDR
L4 ACL Support:
1. Filter a UDP/TCP source port.
2. Filter a UDP/TCP destination port.
Notices:
Maximum profile
: 64.
Maximum profile name length : 16.
The ACL name should be the combination of the digit or the alphabet.
Summary of Contents for NGI-M08C4POE8-2
Page 1: ......
Page 197: ...197 Clear Clear the statistics of the valn ...
Page 298: ...298 9 2 2 Web Configurations ...