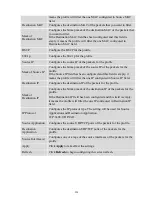
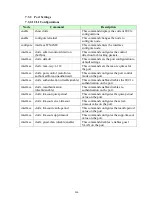
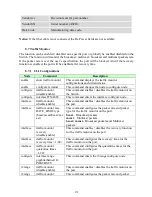
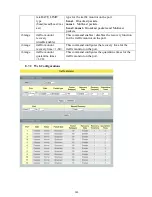
267
7.5
The purpose of this enhancement is to support on the Switch platforms. Terminal
Access Controller Access Control System Plus is a security application that provides centralized
validation of users attempting to gain access to a router, network access server etc. In order for
the feature on the TRIPP LITE products to work it would need a server,
which would typically be a daemon running on a centralized UNIX or windows NT
authentication, authorization and accounting facilities for managing network access points from
a single management service.
Product Features
The implementation will support the following features:
The implementation will conform to version 1.78 of the draft RFC.
Authentication, Authorization and Accounting can be run as well as disabled
independently of each other.
In case authentication fails on account of the server being unreachable the
box can be made to default to a local authentication policy.
packet body encryption will be supported.
Single server will be support.
Multiple connect mode will be support.
Syslog messages will be support.
Functional Description
The implementation will provide the following services:
Authentication:
Complete control of authentication through login and password dialog, challenge and response,
messaging support etc.
Authorization:
Control over user capabilities for the duration of the user session, like setting auto commands,
enforcing restrictions on what configuration commands a user may execute, session duration etc.
Accounting:
Collecting and sending information used for billing, auditing, and reporting to the
daemon.
Each of the above mentioned services can be configured and run independent of the others. The
implementation will provide authentication and confidentiality between the router
and the daemon. It runs on TCP port 49.
Application
Remote network access is witnessing a major paradigm shift that from terminal access to LAN
access. Single users want to connect to the corporate network in the same way that they connect
at work i.e. as a LAN user. This places increased emphasis on network access security. As a result
of this network managers are concerned with 3 parameters: authentication, authorization and
accounting. This is where enters into the picture. A typical deployment using
could be as follow:
Summary of Contents for NGI-M08C4POE8-2
Page 1: ......
Page 197: ...197 Clear Clear the statistics of the valn ...
Page 298: ...298 9 2 2 Web Configurations ...