RCB-F9T - Integration manual
•
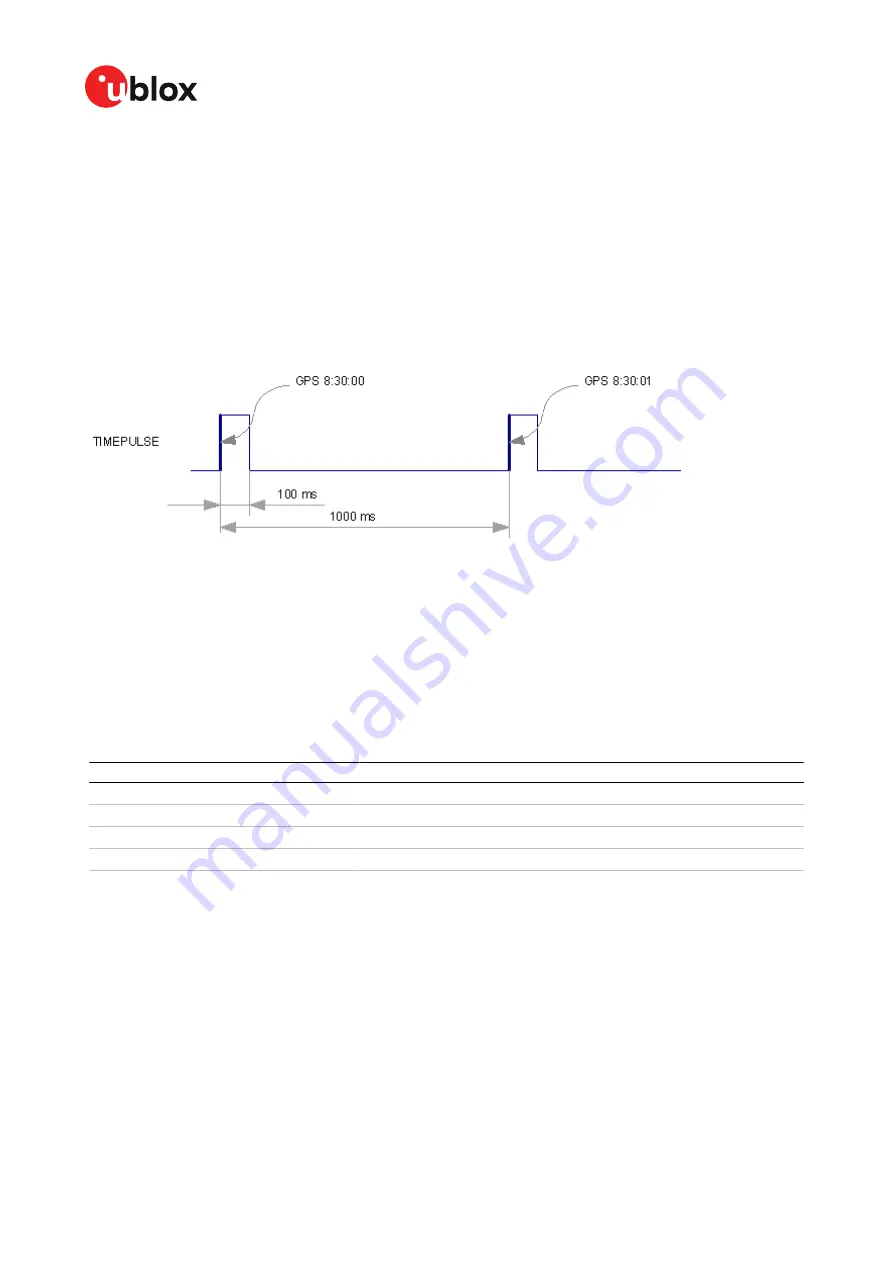
CFG-TP-LEN_TP1
= 100 000 µs
•
CFG-TP-TIMEGRID_TP1
= 1 (GPS)
•
CFG-TP-PULSE_LENGTH_DEF
= 0 (Period)
•
CFG-TP-ALIGN_TO_TOW_TP1
= 1
•
CFG-TP-USE_LOCKED_TP1
= 1
•
CFG-TP-POL_TP1
= 1
•
CFG-TP-PERIOD_LOCK_TP1
= 100 000 µs
•
CFG-TP-LEN_LOCK_TP1
= 100 000 µs
The 1 Hz output is maintained whether or not the receiver is locked to GPS time. The alignment to
TOW can only be maintained when GPS time is locked.
Figure 10: Time pulse signal with the example parameters
3.9 Security
The security concept of RCB-F9T covers the air interface between the receiver and the GNSS
satellites and the integrity of the receiver itself.
There are functions to monitor/detect certain security threads and report it to the host system.
Other functions try to mitigate the thread and allow the receiver to operate normally.
The table below gives an overview about possible threads and which functionality is available to
detect and/or mitigate it.
Threat
u-blox solution
Over air signal integrity
GNSS receiver integrity
Table 11: u-blox security options
3.9.1 Spoofing detection / monitoring
Spoofing is the process whereby someone tries to forge a GNSS signal with the intention of fooling
the receiver into calculating a different user position than the true one.
The spoofing detection feature monitors the GNSS signals for suspicious patterns indicating that
the receiver is being spoofed. A flag in UBX-NAV-STATUS message (flags2 -
spoofDetState
) alerts
the user to potential spoofing.
The spoofing detection feature monitors suspicious changes in the GNSS signal indicating external
manipulation. Therefore the detection is only successful when the signal is genuine first and when
the transition to the spoofed signal is being observed directly. When a receiver is started up
to a spoofed signal the detection algorithms will be unable to recognize the spoofing. Also, the
UBX-19003747 - R04
3 Receiver functionality
Page 33 of 54
Early production information
















































