56
Web User Interface
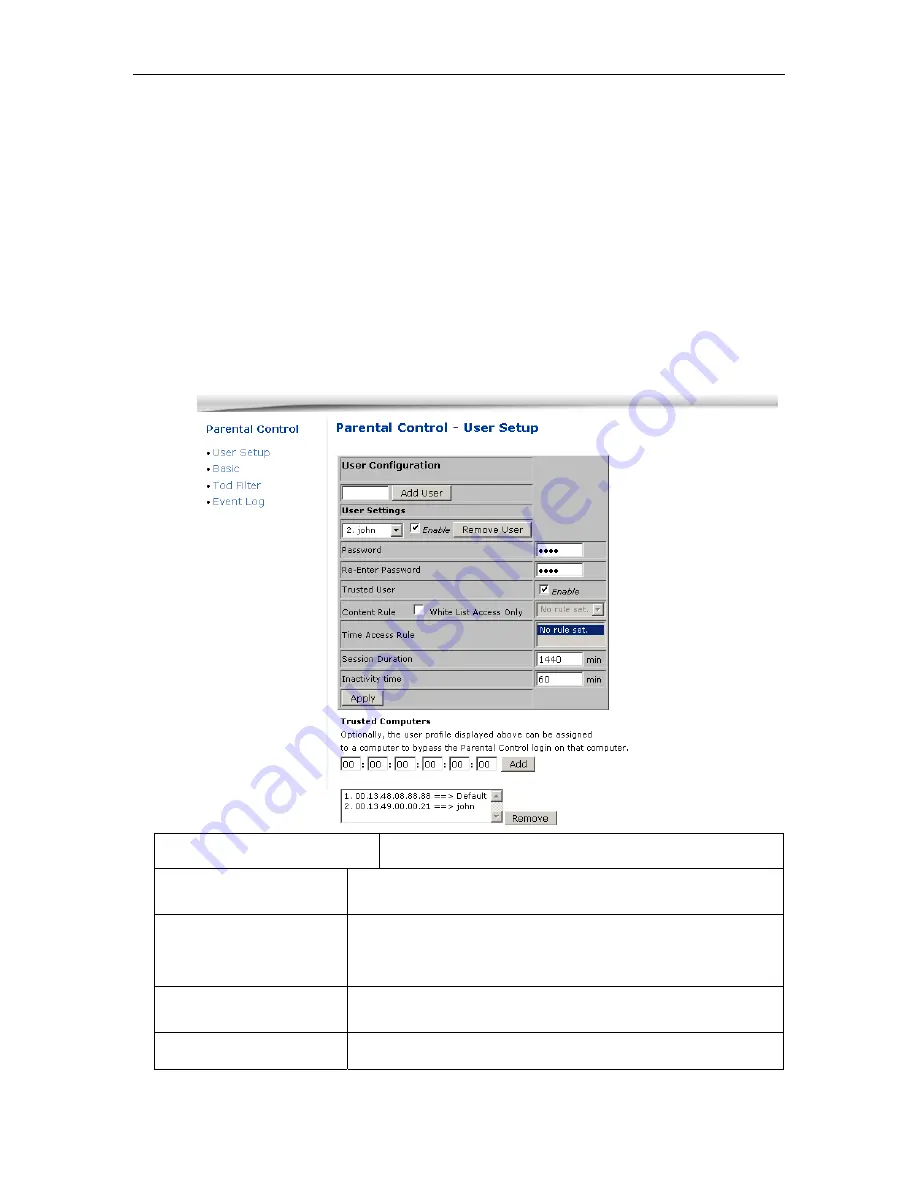
to allow a finite amount of time that a user has Internet access via the rules entered once
entering their password to get to the Internet for the first time. This allows access to the Internet for
a defined user without having to enter a password every time a new web page is served to the
client. Likewise, there is a password inactivity timer if there is no Internet access for the specified
amount of time in minutes, requiring the user to re-login at expiration to continue using the Internet.
These timed logins insure that a specific user is using the Internet gateway for access and
logging/access can be provided appropriately. Any time a change is made on this page for a
particular user, the Apply button at the bottom of the page needs to be pressed to activate and
store the settings.
Label Description
User configuration
Input username to create a new user.
Add user
Click to direct add this user into local database even you
haven’t finished the configuration for this user.
User Settings
Enable
Click to active this user account, and to modify current
U10C019/U10C020
















































