aXsGUARD Identifier 3.0.2.0 Product Guide v1.5
User Authentication Process
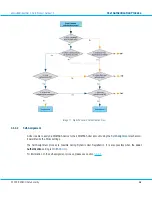
Image 12: Password Replacement with an IIS Module
3.6.3.4
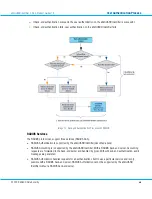
Stored Static Password and RADIUS Attributes
The purpose of this setup is to enforce DIGIPASS OTP authentication to an existing RADIUS client and server
infrastructure, without losing the RADIUS attribute functionality. This is achieved by configuring the RADIUS client to
authenticate towards the aXsGUARD Identifier and configuring a RADIUS back-end server record on the aXsGUARD
Identifier for the RADIUS server.
After these configurations, the DIGIPASS OTP authentication requests from the RADIUS client are verified by the
aXsGUARD Identifier. After successful authentication on the aXsGUARD Identifier, the stored static password is
forwarded to the RADIUS back-end server, and the required RADIUS attributes are retrieved. These attributes are
forwarded by the aXsGUARD Identifier to the RADIUS client, which completes the authentication request (see image
below).
The RADIUS Server password (the static password) only needs to be supplied by the User on first-time use, and
when modified, because it is stored in the DIGIPASS User Account on the aXsGUARD Identifier.
©
2009 VASCO Data Security
43