Personal aXsGUARD - 7.7.1
Chapter 4. Server-Side Configuration
© VASCO Data Security 2013
16
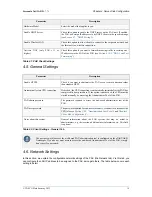
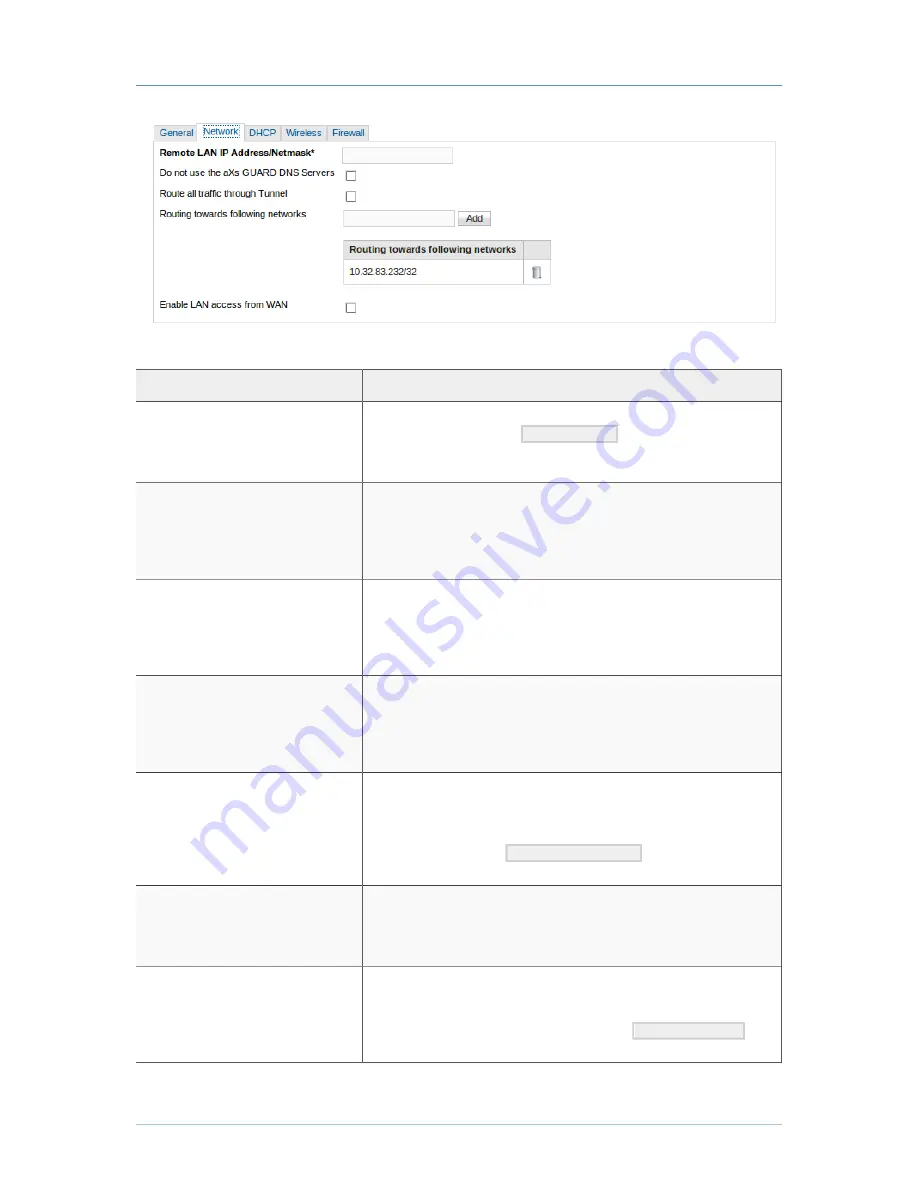
Figure 4.3. PAX Network Settings
Parameter
Description
Remote LAN IP – Address Netmask
This is the LAN IP address and subnet mask to be assigned to the PAX.
Use the CIDR notation, e.g.
10.0.0.1/24
. Use the IP address specified
here to access the web-based Administrator Tool of the PAX (explained in
Chapter 5, Client-Side Configuration
).
Do not use the aXsGUARD DNS
Servers
(See note below) Leave this option unchecked if you want to use the
aXsGUARD Gatekeeper DNS server while the VPN tunnel is up. Check
this option if you are using another DNS server (not the aXsGUARD
Gatekeeper), e.g. an Active Directory DNS server. You can specify one or
multiple DNS servers using the Add button.
DNS Server IP list
(See note below ) If the Do not use the aXsGUARD DNS Servers option is
selected, this field becomes available so you can enter the IP address(es) of
the DNS server(s) to be used while the VPN tunnel is up, i.e. DNS servers
other than the aXsGUARD Gatekeeper. Use the Add button to enter the IP
address(es).
Route all traffic through Tunnel
If this option is selected, all traffic leaving the PAX’s client is routed via the
VPN tunnel, including traffic towards the Internet. As a result, the corporate
aXsGUARD Gatekeeper acts as an Internet / network Gateway If this option
is unchecked, traffic towards the Internet is routed via the default gateway
of the PAX’s client.
Routing
towards
the
following
networks
Specify the networks which must be accessible via the VPN connection.
By default, the IP address of the aXsGUARD Gatekeeper’s primary LAN
interface is already provided. You must manually add the network address
of any other networks that must be accessible via the VPN connection. Use
the CIDR notation, e.g.
192.168.230.0/24
. Use the Add button to
enter the network address(es).
Enable WAN to LAN in NAT setup
Check this option if the WAN interface of your PAX is connected to a
NAT’d network segment and you wish to grant access to the PAX’s LAN
from hosts of this NAT’d segment, as explained in
Section 3.4, “NAT
Traversal”
.
Allow access from these networks to
LAN
If the option Enable LAN access from WAN is enabled, you must specify the
network address of the NAT’d network segment which is allowed to connect
the PAX’s LAN (see
Section 3.4, “NAT Traversal”
for more details). Use
the CIDR notation to specify the network, e.g.
172.16.0.0/24
. Use
the Add button to enter the network addresses.
Table 4.3. PAX Client Settings - Network Tab