aXsGUARD Identifier 3.0.2.0 Product Guide v1.5
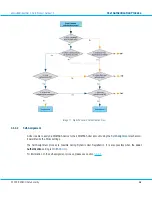
User Authentication Process
The time between retries is a few minutes, i.e. long enough to ensure that a temporary delayed response due to a
peak load does not prevent a back-end server from being used. A consistent lack of response for the set number
of retries causes the back-end server not be used for a pre-defined length of time, if an alternative is available.
After this pre-defined length of time, the aXsGUARD Identifier retries once again.
3.6.4.2
Domain-specific Back-end Servers
Back-end server records may be configured for use with a specific
Domain
. This may be useful when multiple
back-end servers exist with different groups of User records on each.
When the aXsGUARD Identifier needs to choose a back-end server, it searches for records in the domain identified
by the
User ID and Name Resolution
). If any are found, it only uses the back-end
servers for that domain. If none are found, it uses the back-end servers which are not assigned to a domain.
3.6.5
RADIUS Back-end Authentication
aXsGUARD Identifier supports RADIUS back-end authentication (see also section
). A RADIUS back-end
server record contains connection information for the RADIUS server, including location details and the RADIUS
Shared Secret
. It also allows a
Timeout
and
No. of Retries
to be configured.
User ID Formats
User ID formats possible with RADIUS back-end authentication are shown in the table below.
Table 3: RADIUS User ID Formats for Back-end Authentication
User ID Format
Example
With domain
geraard@domain.com
geraard
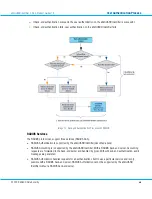
Authentication Process
There are two steps to back-end authentication with RADIUS (see image below):
1.
First the back-end server for authentication needs to be identified. A User ID can be provided for
authentication with or without inclusion of the domain reference (i.e. the
' part).
If the domain is included and exists, the back-end server for the domain is identified.
If the domain is not included, or is included but does not exist, and a default domain is specified in the policy
for the client, the back-end server for the default domain is identified.
If the domain is not included, or is included but does not exist, and a default domain is not specified in the
policy for the client, the back-end server for the Master domain is identified.
2.
Once the back-end server is identified, back-end authentication can be completed using the User ID and
password provided with the authentication request:
©
2009 VASCO Data Security
45