_______________________________________________________________________________________________________
_______________________________________________________________________________________________________
© Virtual Access 2018
GW2020 Series User Manual
Issue: 2.1
Page 301 of 423
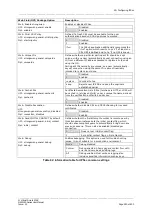
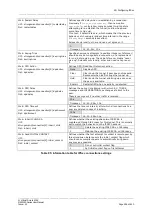
Traffic originated on
remotelan
and destined to
locallan
address is excluded from VPN
IPSec policy.
29.3.4
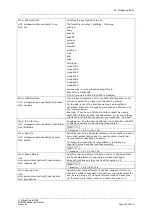
Secret settings
Each tunnel also requires settings for how the local end point of the tunnel proves its
identity to the remote end point.
A sample secret section, which could be used with the connection section in ‘Connection
Settings’, is shown below.
# Commands to add a secret for psk auth
touch /etc/config/strongswan
uci add strongswan secret
uci set strongswan.@secret[0].enabled=yes
uci set strongswan.@secret[0].localaddress=192.168.209.1
uci set strongswan.@secret[0].remoteaddress= 100.100.100.100
uci set strongswan.@secret[0].secrettype=psk
uci set strongswan.@secret[0].secret=secret
uci commit
This will create the following output:
config secret
option enabled 'yes'
option localaddress '192.168.209.1'
option remoteaddress '100.100.100.100 '
option secrettype 'psk'
option secret 'secret'
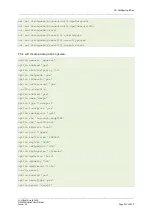
If xauth is defined as the authentication method then you must include an additional
config secret section, as shown in the example below.
# Commands to add a secret for xauth auth
touch /etc/config/strongswan
uci add strongswan secret
uci set strongswan.@secret[1].enabled=yes
uci set strongswan.@secret[1].idtype=userfqdn
uci set strongswan.@secret[1].userfqdn=testxauth
uci set strongswan.@secret[1].remoteaddress=100.100.100.100
uci set strongswan.@secret[1].secret=xauth