CHAPTER 9: Security Policy Examples
218
Vcontroller
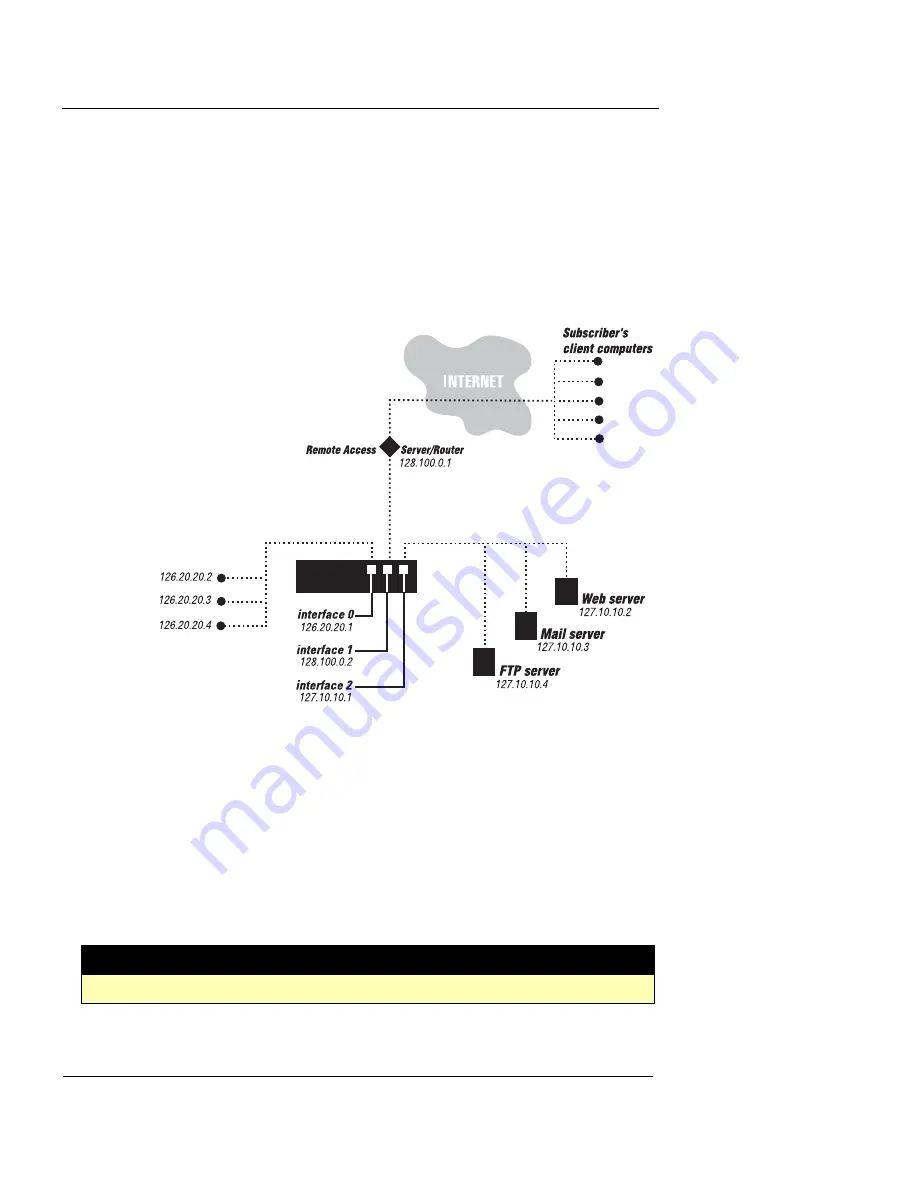
Example 5: Defining policies for an ISP
ConnectYouUp.com is an ISP with a firewall that both pro-
tects all internal private network assets while permitting
access by subscribers to servers in a DMZ, reading and
sending email, surfing the Internet, and taking advantage
of FTP services.
In such a network environment, you may want to create a
number of complementary policies that permit access by
certain users to a limited set of assets (servers), while per-
mitting free external access to all internal users.
1
Open the
System Configuration
dialog box and use
the
Route
tab features to add a new route to the
appliance. The new route represents the default
gateway, which is the remote access server/router.
.
Destination
Net Mask
Gateway
Interface
Metric
0.0.0.0
0.0.0.0
128.100.0.1
1
1
Summary of Contents for Firebox V10
Page 1: ...WatchGuard Firebox Vclass User Guide Vcontroller 5 0 ...
Page 32: ...xxxii Vcontroller ...
Page 40: ...CHAPTER 1 Introduction 8 Vcontroller ...
Page 52: ...CHAPTER 2 Service and Support 20 Vcontroller ...
Page 70: ...CHAPTER 3 Getting Started 38 Vcontroller ...
Page 110: ...CHAPTER 4 Firebox Vclass Basics 78 Vcontroller ...
Page 190: ...CHAPTER 7 Using Account Manager 158 Vcontroller ...
Page 268: ...CHAPTER 9 Security Policy Examples 236 Vcontroller ...
Page 410: ...CHAPTER 14 Monitoring the Firebox Vclass 378 Vcontroller ...
Page 456: ...CHAPTER 18 Using the Diagnostics CLI Feature 424 Vcontroller ...




































